All-in-one IP monitoring tool for your entire network
- Check reachability of network devices
- Break down & analyze traffic by IP address
- Use PRTG as your IP Sniffer and IP traffic monitor
PRTG makes IP monitoring easy
Custom alerts and data visualization make it easy to monitor, identify, and prevent IP traffic issues.
The PRTG IP monitoring advantage: 4 handy use cases
How PRTG defines sensors
In PRTG, “sensors” are the basic monitoring elements. One sensor usually monitors one measured value in your network, e.g. the traffic of a switch port, the CPU load of a server, the free space of a disk drive. On average you need about 5-10 sensors per device or one sensor per switch port.
Automatically discover new network devices
Paessler PRTG makes it easy for you to take stock of your IT infrastructure. It automatically discovers all network devices within a specified IP address range and adds them to your monitoring setup. This way, you can not only save lots of time, but also find out if there are devices connected to your network that should not be there at all.
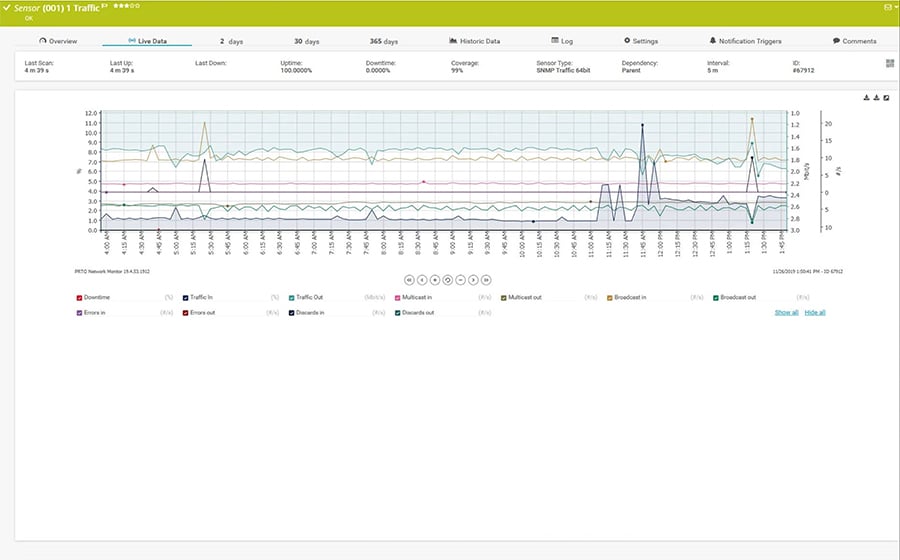
Check if your network devices are reachable
If you want to see if your devices are reachable over the network or the internet, just use the Ping v2 or the Cloud Ping v2 sensors in PRTG. These sensors ping the IP address of a device and immediately notify you if the device is not available as expected. This way, you can react as quickly as possible and fix the issue before it becomes business critical.
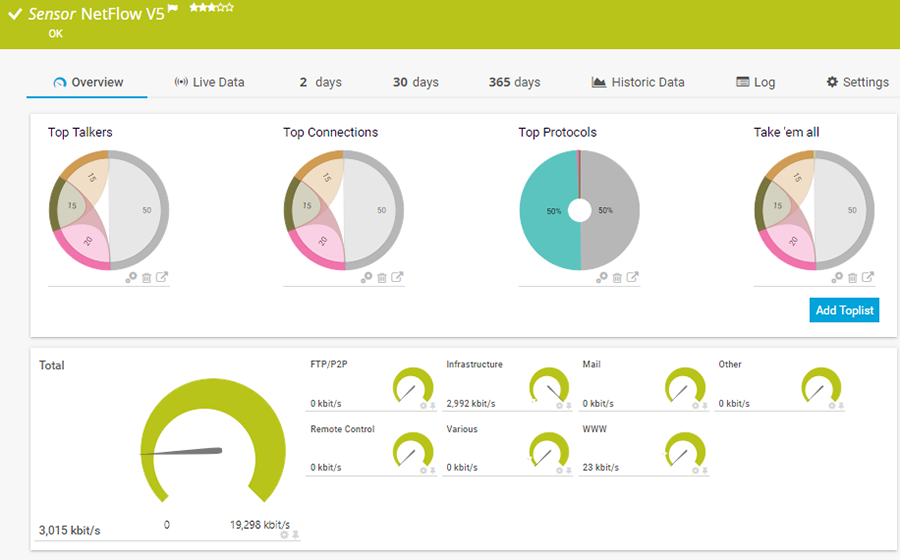
Identify the top talkers in your network
With our Packet Sniffer and Flow (NetFlow, jFlow, sFlow, IPFIX) sensors, you can easily identify bottlenecks in your network while keeping an eye on network security at the same time. These sensors break down and visualize network traffic by IP address, port, or protocol so that you can pinpoint the IP addresses that consume the most bandwidth in your LAN at a quick glance.
Keep an eye on correct name resolution
Measure the response time of your DNS server and make sure that it is protected against attacks over the internet using the DNS v2 sensor. This sensor resolves domain name records and compares them to a filter. This way, you can make sure that no one has compromised the DNS cache to redirect employees or customers to malicious websites, for example.
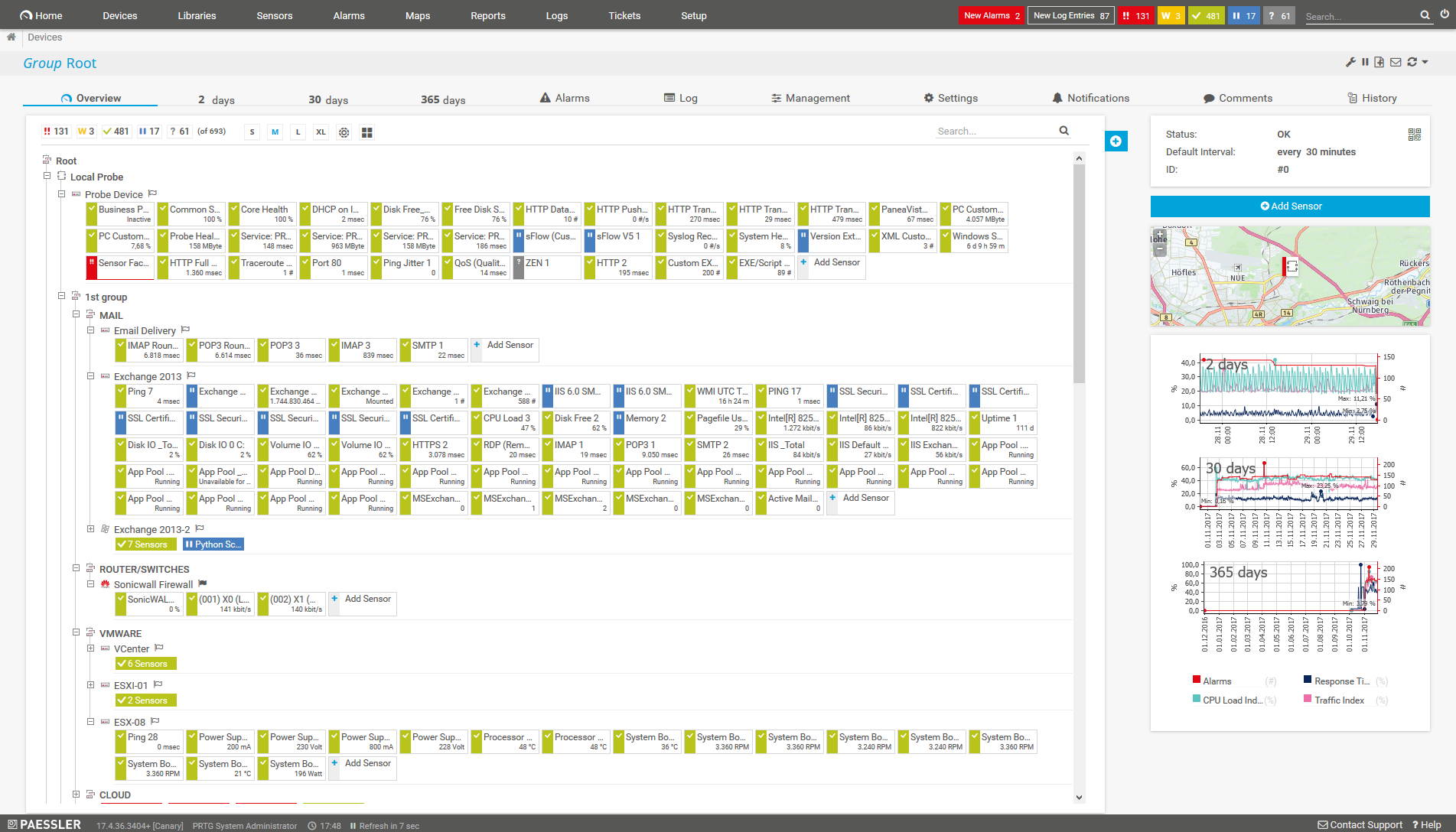
What IP monitoring looks like in PRTG
Diagnose network issues by continuously pinging the IP addresses of your network devices. Show traffic by IP address in almost real time and visualize data in graphic maps & dashboards to identify problems more easily. Gain the visibility you need to troubleshoot IP monitoring issues.
Start IP address monitoring with PRTG and see how it can make your network more reliable and your job easier.
Benefit from comprehensive IP traffic monitoring
As an administrator, you want to keep a close eye on your network traffic. And for good reason: one single IP address can use up so much bandwidth that this might ultimately have negative consequences for your entire IT infrastructure. Thanks to our IP monitoring tool PRTG, you will prevent traffic problems over the long term and thus optimize the performance of your network.
Overview of total network traffic
How much traffic passes through your network in total? The SNMP Traffic sensor shows you, for example, the total amount of traffic as well as the incoming and outgoing traffic on your network devices.
Does the Christmas season put added pressure on your online store? With the PRTG IP monitoring solution, you can identify weekly, monthly, and seasonal fluctuations in your network traffic. You'll see how traffic develops over longer periods of time and take measures to adapt bandwidth capacities accordingly.
Detailed traffic by IP address
You can also have a look at your network traffic in greater detail. Via Packet Sniffing, with NetFlow sensors for Cisco devices, or with other flow technologies like sFlow or jFlow, you can analyze your traffic more precisely and fine-tune your IP monitoring.
The sensors display the amount of mail and web traffic, the traffic generated by file transfers or chat protocols, and much more. Where does such data come from? Who is the recipient? Which protocols are used? You can find an answer to all these questions using our IP traffic monitor.
Get your free copy of our IPv6 cheat sheet now.
3 reasons why PRTG is the right IP monitoring tool for you
Create your own network visualizations
Always know what’s going on in your network – either by looking at the central dashboard that shows your infrastructure as a hierarchical device tree, or by creating custom maps and dashboards with our easy-to-use drag-and-drop editor.
PRTG uses a simple traffic lights system to warn you (yellow), alert you (red), or show you that everything is working just fine (green). This way, you can see at a quick glance if there is an issue that needs your attention.
Receive custom alerts and notifications
With PRTG, you can easily set custom warning and error thresholds that suit your individual monitoring requirements. Define, for example, notification triggers to make sure that the right team is informed as soon as a threshold is exceeded.
In addition, choose from various communication channels such as email, SMS, Teams message, push notification, and more. This way, you can rest assured that if PRTG doesn’t alert you, there’s no issue to solve.
Get started quickly with built-in sensors
PRTG comes with over 250 preconfigured sensors for monitoring your network devices from the most popular manufacturers as well as your entire IT infrastructure out-of-the-box.
Choose the sensors that you need for your specific requirements – no matter if you want to keep an eye on your on-premises or cloud environment, your server hardware or virtual servers, your websites, and much more.
Easily find the source of the problem with our PRTG IP monitoring solution
Real-time alerts and custom notifications make it easy to solve issues with IP monitoring.
PRTG can do more than IP monitoring for you
SLA monitoring
Make sure that you comply with your service level agreements by preventing malfunctions and downtimes. Implement IP SLA monitoring, for example, and check the quality of your VoIP connections round the clock.
VPN monitoring
Monitor your VPN connections and measure network traffic, load, and the number of logged-in users. Identify connection problems and suspicious traffic before they cause real trouble for your customers or colleagues.
Network security monitoring
Always keep an eye on your firewalls, ports, servers, and other important aspects of your IT infrastructure to maintain the security of your network. Custom alerts notify you in real time about irregularities in your environment.
PRTG is compatible with all major vendors, products, and systems
Your IP check at a glance – even on the go
Set up PRTG in minutes and use it on almost any mobile device.
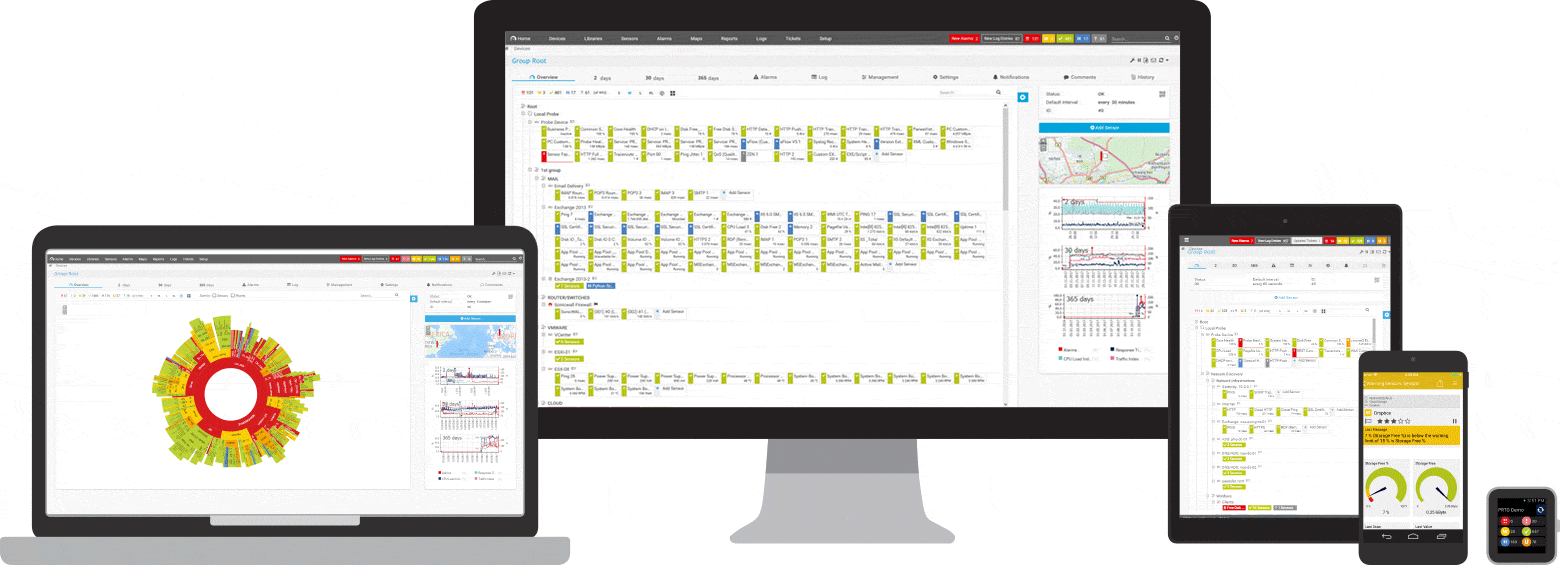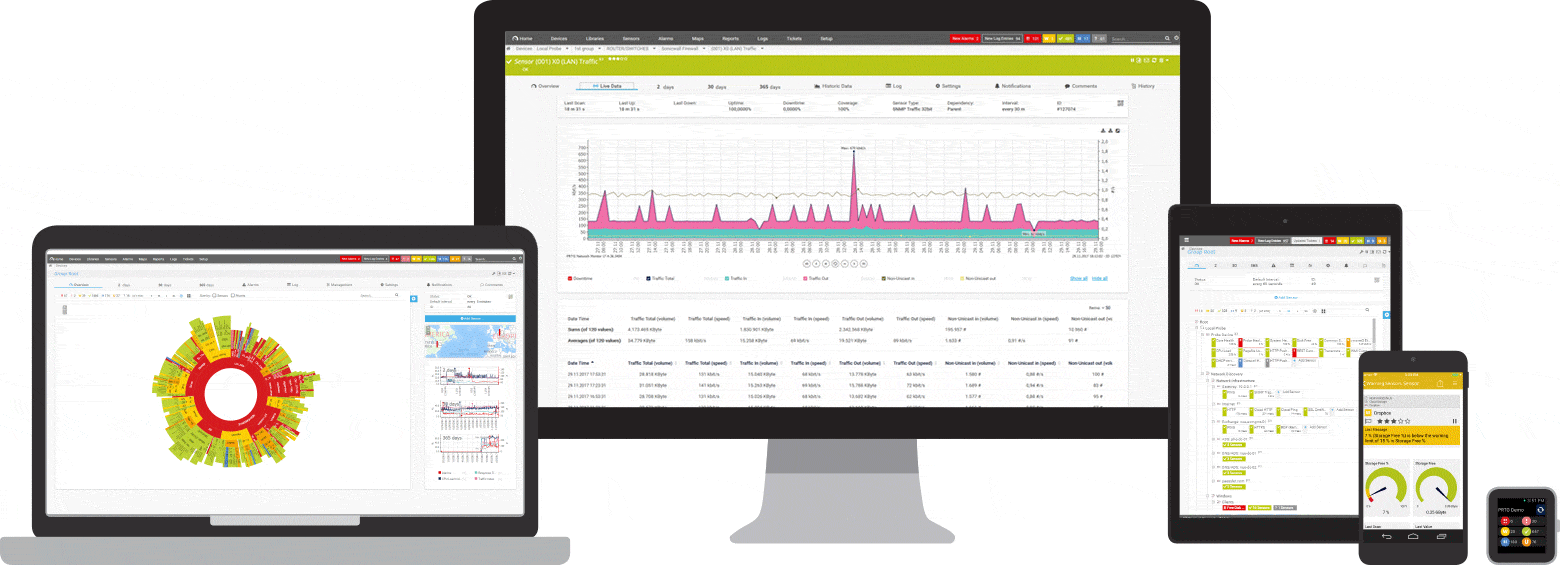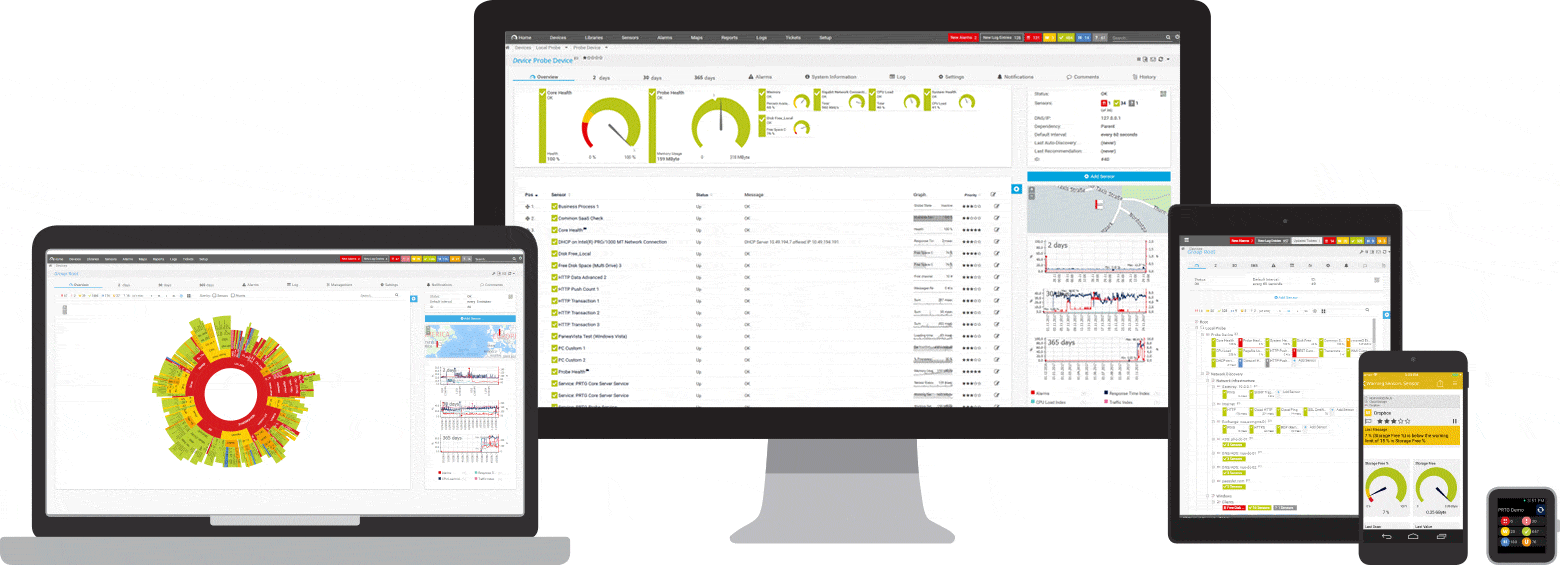

PRTG makes IP monitoring easy
Custom alerts and data visualization make it easy to monitor, identify, and prevent IP traffic issues.
Create innovative solutions with Paessler’s partners
Partnering with innovative vendors, Paessler unleashes synergies to create
new and additional benefits for joined customers.
With ScriptRunner, Paessler integrates a powerful event automation platform into PRTG Network Monitor.
ScriptRunner
Oliver Jähn, IT Manager at the University of Bonn![]()
“For us, PRTG Network Monitor is the most effective tool for monitoring our IT infrastructure in the long run.”
We'll make you a monitoring expert
Gain practical knowledge on how to monitor your infrastructure with Paessler PRTG. Our training sessions are planned and provided by Paessler system engineers and are suitable for different experience levels.
PRTG: The multi-tool for sysadmins
Adapt PRTG individually and dynamically to your needs and rely on a strong API:- HTTP API: Access monitoring data and manipulate monitoring objects via HTTP requests
- Custom sensors: Create your own PRTG sensors for customized monitoring
- Custom notifications: Create your own notifications and send action triggers to external systems
- REST Custom sensor: Monitor almost everything that provides data in XML or JSON format
PRTG makes IP monitoring easy
Custom alerts and data visualization make it easy to monitor, identify, and prevent IP traffic issues.
We asked: would you recommend PRTG?
Over 95% of our customers say yes!
Paessler conducted trials in over 600 IT departments worldwide to tune its network monitoring software closer to the needs of sysadmins.
The result of the survey: over 95% of the participants would recommend PRTG – or already have.
Paessler PRTG is used by companies of all sizes. Sysadmins love PRTG because it makes their job a whole lot easier. Bandwidth, servers, virtual environments, websites, VoIP services – PRTG keeps an eye on your entire network. Everyone has different monitoring needs. That’s why we let you try PRTG for free.Still not convinced?
More than 500,000
sysadmins love PRTGMonitor your entire IT infrastructure
Try Paessler PRTG
for free
Start IP address monitoring with PRTG and see how it can make your network more reliable and your job easier.
|
PRTG |
Network Monitoring Software - Version 24.2.96.1375 (June 26th, 2024) |
|
Hosting |
Download for Windows and cloud-based version PRTG Hosted Monitor available |
Languages |
English, German, Spanish, French, Portuguese, Dutch, Russian, Japanese, and Simplified Chinese |
Pricing |
Up to 100 sensors for free (Price List) |
Unified Monitoring |
Network devices, bandwidth, servers, applications, virtual environments, remote systems, IoT, and more |
Supported Vendors & Applications |
|









Combining the broad monitoring feature set of PRTG with IP Fabric’s automated network assurance creates a new level of network visibility and reliability.