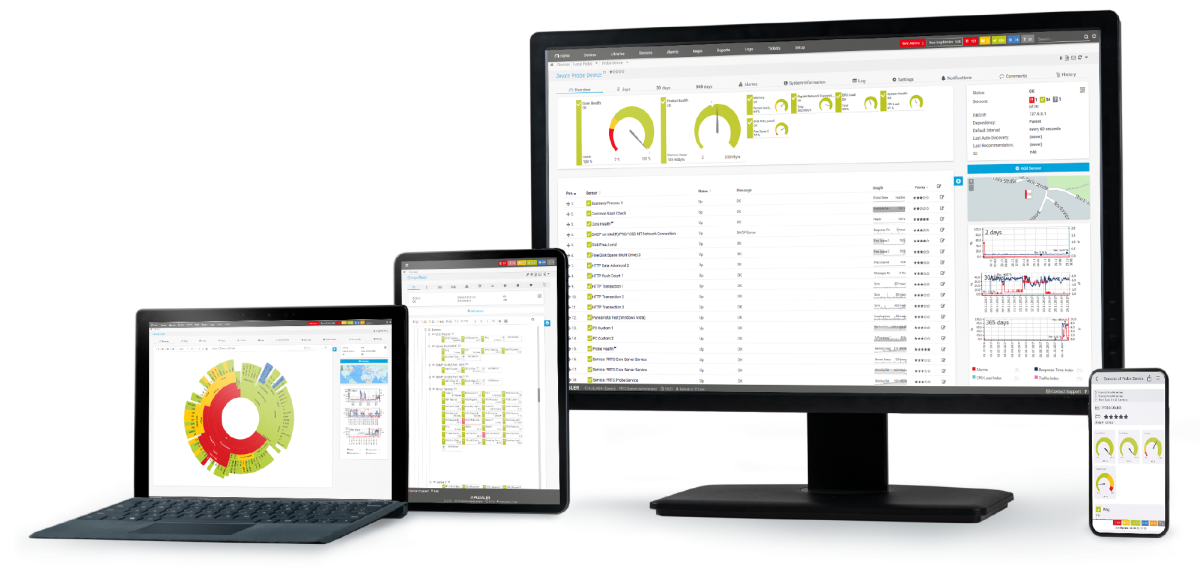
Custom alerts and data visualization let you quickly identify and prevent cybersecurity issues.
Keeping your servers and data secure is critical for your organization to function. You need to ensure the confidentiality, integrity, and availability of all data and services across the organization. Paessler PRTG’s server security monitoring software is your 24/7/365 security detail for your entire IT infrastructure.
Quickly identify potential network bottlenecks and unusual spikes in traffic. PRTG uses SNMP, packet sniffing, and flow protocols like NetFlow to detect suspicious activities that can indicate a security breach.
In the case of unusual or suspicious activity, PRTG helps you isolate servers or selectively disable applications for a targeted response.
Set up PRTG to perform automated integrity checks of your files, folders, and logs. This way, you can uncover modifications to files or unusual log data that might otherwise be overlooked.
PRTG notifies you in case of any changes to your data that deviate from the norm, and alerts you via custom notifications so that you can react as quickly as possible to mitigate the potential threat.
Get a hold of your entire IT environment (on-premises or cloud-based) for robust security, including firewalls, anti-virus software, and other security measures.
With PRTG's network monitoring system, you can keep weak or even blind spots to a minimum by making sure that you have a 360° overview of all your systems and applications – all from a single dashboard.
Protect your servers and infrastructure against potential threats with physical security mechanisms. PRTG lets you keep an eye on electronic door locks or CCTV security cameras to prevent unauthorized access.
Even environmental parameters such as temperature and humidity can be monitored to protect your servers from hardware damage.
Diagnose network issues by continuously tracking server performance and security events. Show server health, bandwidth usage, response time, uptime, disk space, CPU utilization, latency, and other key performance metrics in real time. Visualize the collected data in clear graphs and dashboards to identify problems more easily. Gain the overview you need to troubleshoot downtime, data loss, and overall performance issues.
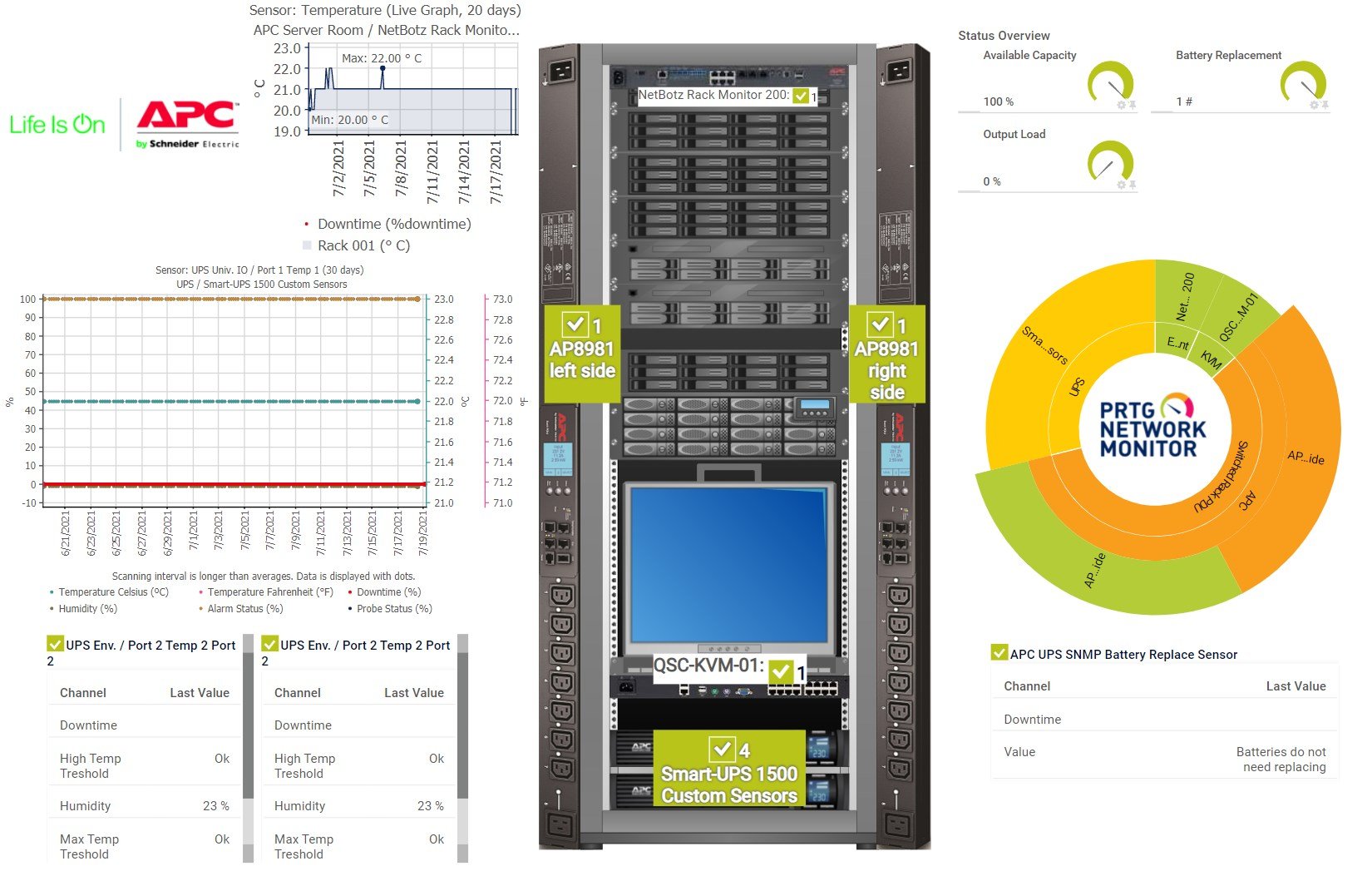
APC Infrastructure Monitoring with PRTG – Live UPS, Temperature, and Battery Status
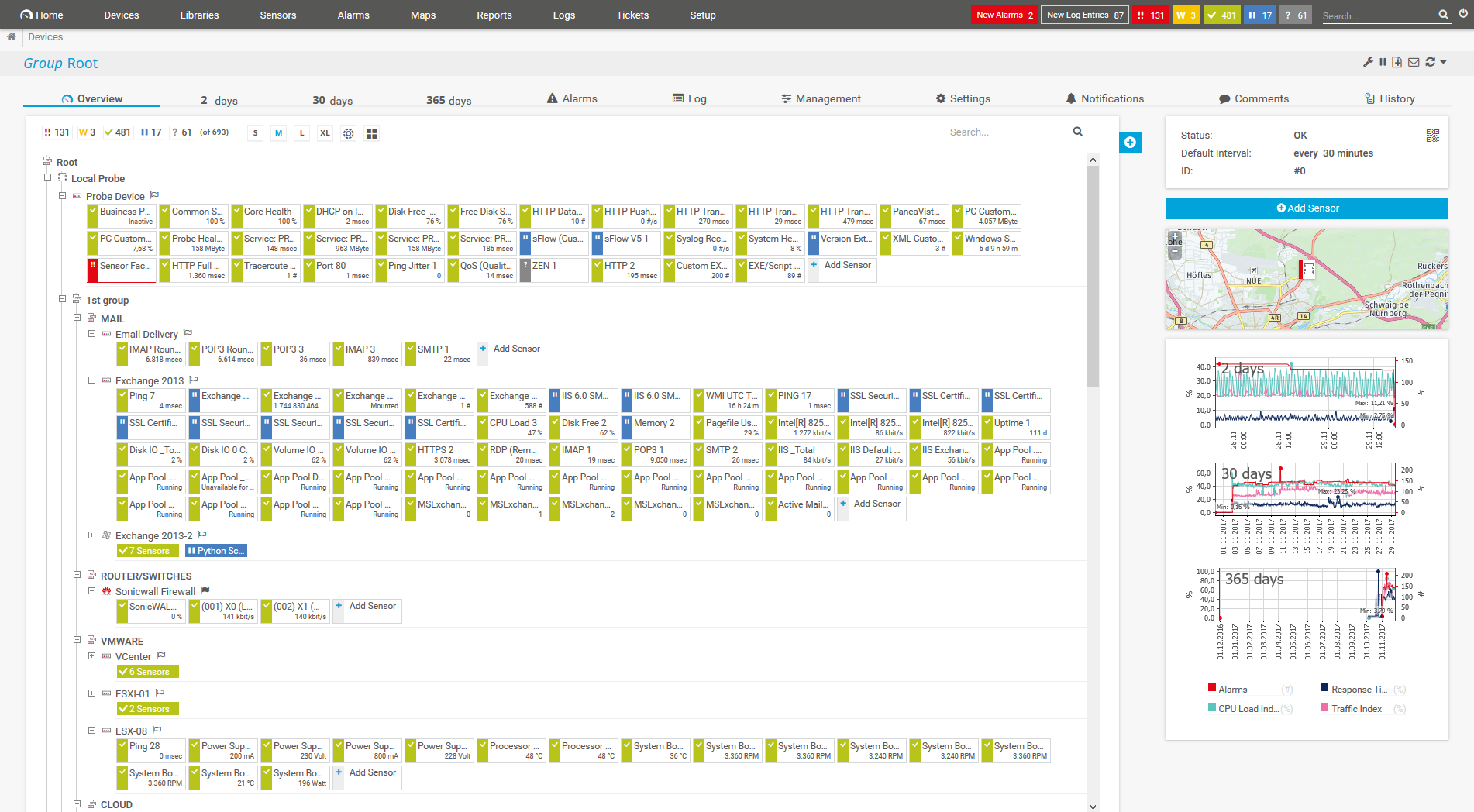
Device tree view of the complete monitoring setup
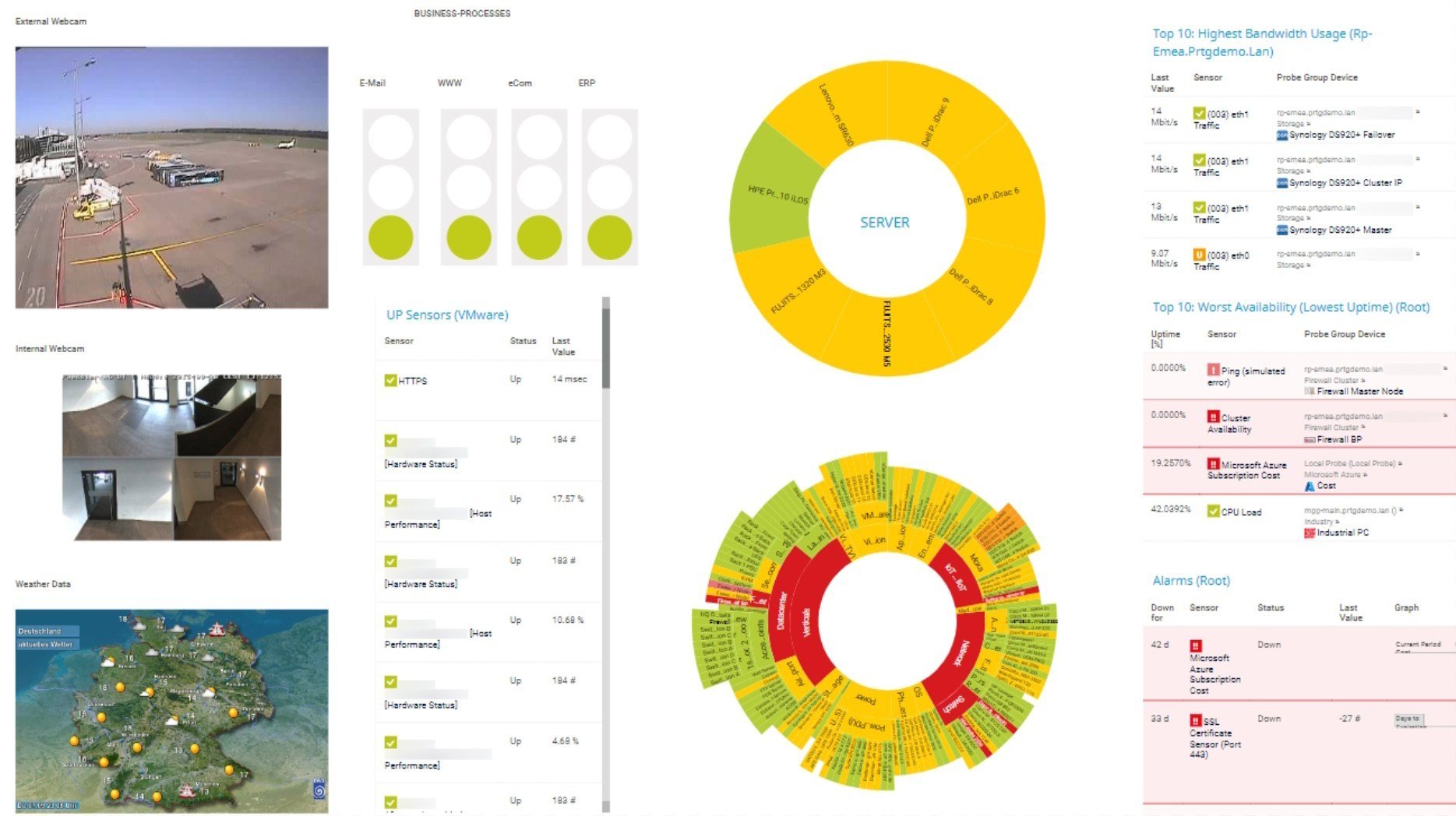
Custom PRTG dashboard for keeping an eye on the entire IT infrastructure
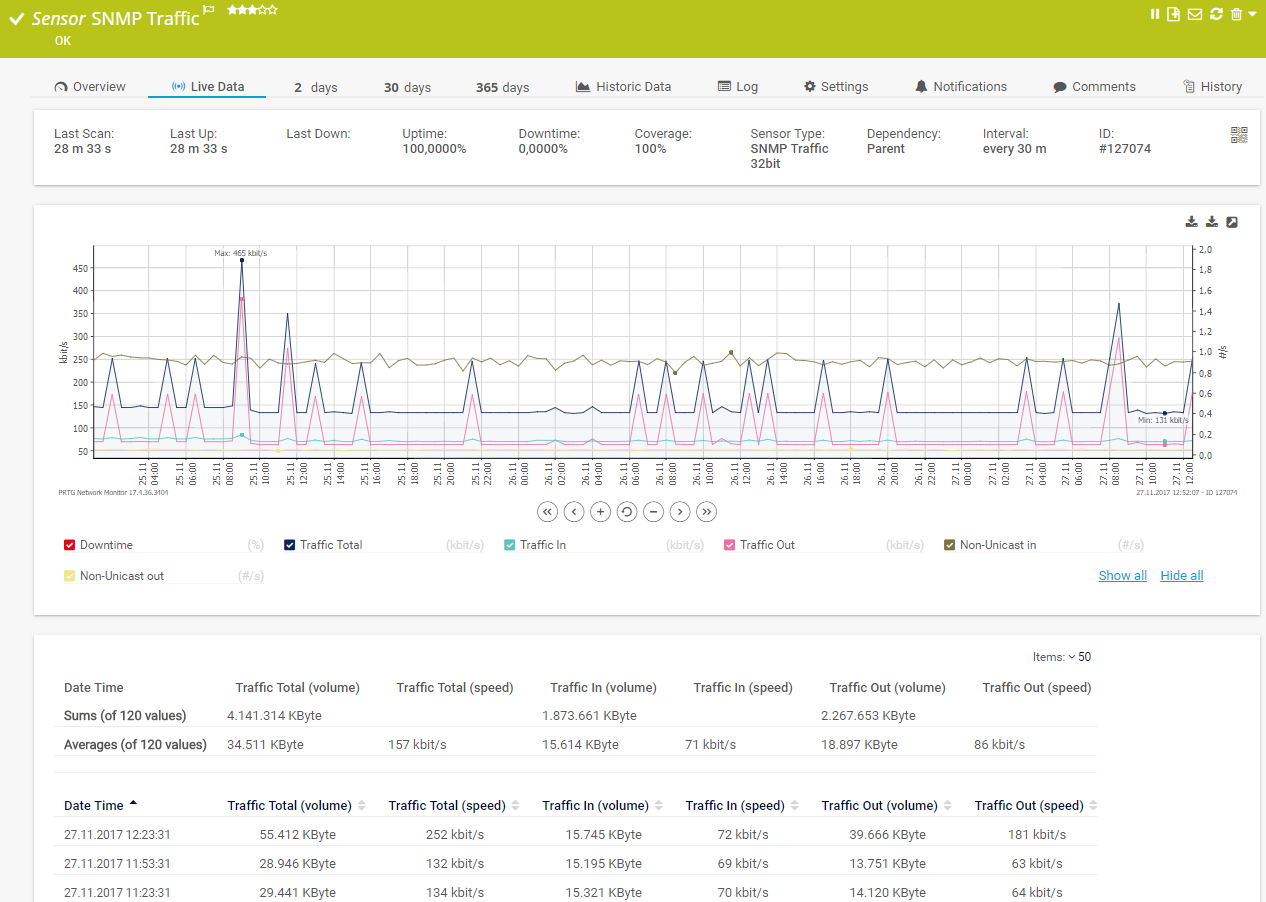
Live traffic data graph in PRTG
PRTG comes with more than 250 native sensor types for monitoring your entire on-premises, cloud, and hybrid cloud environment out of the box. Check out some examples below!
See the PRTG Manual for a list of all available sensor types.
Custom alerts and data visualization let you quickly identify and prevent cybersecurity issues.
PRTG is set up in a matter of minutes and can be used on a wide variety of mobile devices.
As one of the leading players in the IT monitoring industry, Paessler has also become an authorized Dell partner for building integrated solutions around the Dell technology ecosystem.
What does this mean for you?
Partnering with innovative IT vendors, Paessler unleashes synergies to create
new and additional benefits for joined customers.
baramundi and PRTG create a secure, reliable and powerful IT infrastructure where you have everything under control - from the traffic in your firewall to the configuration of your clients.
With ScriptRunner Paessler integrates a powerful event automation platform into PRTG Network Monitor.
UVexplorer integrates tightly with PRTG to bring fast and accurate network discovery, detailed device inventory, and automatic network mapping to the PRTG platform.
Real-time notifications mean faster troubleshooting so that you can act before more serious issues occur.
Network Monitoring Software – Version 25.3.110.1313 (August 27, 2025)
Download for Windows and cloud-based version PRTG Hosted Monitor available
English, German, Spanish, French, Portuguese, Dutch, Russian, Japanese, and Simplified Chinese
Network devices, bandwidth, servers, applications, virtual environments, remote systems, IoT, and more
Choose the PRTG Network Monitor subscription that's best for you
Server security monitoring is the continuous process of tracking, analyzing, and assessing the security of a server to ensure it is protected from unauthorized access, attacks, or other malicious activities. The goal of server security monitoring is to detect security incidents early, respond quickly, and prevent potential threats from compromising the server or the data it hosts.
Key aspects of server security monitoring include:
Yes. Whether you have just a few servers or a gigantic server farm, PRTG adapts to the size of your server landscape. With PRTG’s powerful auto-discovery feature, even virtual servers are recognized automatically and incorporated into your monitoring environment.
No. Antivirus software should always be installed to defend against viruses and other malware. However, PRTG can keep an eye on the availability and functionality of your antivirus software and thus ensure that it does its job.
Yes. PRTG includes server room monitoring and helps you protect your server room from threats and damage due to unauthorized access or fluctuations in temperature and humidity. PRTG provides sensors that constantly monitor the health of your important servers and hardware, protecting your server room from power interruptions, malfunctioning air conditioners, smoke, and fire.
In PRTG, “sensors” are the basic monitoring elements. One sensor usually monitors one measured value in your network, for example the traffic of a switch port, the CPU load of a server, or the free space on a disk drive. On average, you need about 5-10 sensors per device or one sensor per switch port.
Paessler conducted trials in over 600 IT departments worldwide to tune its network monitoring software closer to the needs of sysadmins. The result of the survey: over 95% of the participants would recommend PRTG – or already have.
Paessler PRTG is used by companies of all sizes. Sysadmins love PRTG because it makes their job a whole lot easier.
Bandwidth, servers, virtual environments, websites, VoIP services – PRTG keeps an eye on your entire network.
Everyone has different monitoring needs. That’s why we let you try PRTG for free.