Custom alerts and data visualization let you quickly identify and prevent unauthorized file changes, suspicious activity, and other potential security threats.
Firewalls, VPNs, anti-malware, and other enterprise network security controls aren’t infallible.
That’s the bad news.
The good news is that, should bad actors manage to find their way around them and gain unauthorized access to your network, you can still stop them in their tracks.
Which is where PRTG’s file integrity monitoring solution comes in.
Like a powerful CCTV system, PRTG stays trained on your files, continuously monitoring who is accessing them, and ensuring no unexpected file modifications go undetected. And, the quicker you’re able to get in front of potential cyber threats, the easier it will be to neutralize them before they do lasting damage to your organization.
Windows registry files. Active Directory files. Databases. Operating system files. Log files. Boot-up files. PRTG can monitor every single file on your network, whether it's stored locally, in the cloud, or in virtualized environments, so you always know who's accessing them and what changes they've made.
Bad actors might get around firewalls and other cybersecurity measures, but system files don't lie. PRTG alerts you about unauthorized access and unexpected file changes straight away. And, because it has a change intelligence framework built in, you won't get flooded with false positives.
Protect your files from tampering and improve your security posture without adding to your to-do list. Design a tailor-made policy for surgical file integrity monitoring across your entire network, and bring all your critical data in one place to simplify threat detection, remediation, and regulatory compliance.
Subject to GDPR, HIPAA, or other regulations, or need to follow standards like PCI DSS or CIS security benchmarks? With PRTG's file integrity monitoring software keeping an eye out for unauthorized changes, you can show regulators and industry bodies you're dead serious about following best practice.
Diagnose network issues by continuously tracking application files, configuration files, system files, event logs, user permissions, registry keys, and other critical system data. Show changes to files, their frequency, volume, and other key metrics in real time. Visualize monitoring data in clear graphs and dashboards to identify problems more easily. Gain the overview you need to detect and prevent unauthorized file changes, suspicious activity, and other potential security threats to your IT infrastructure.
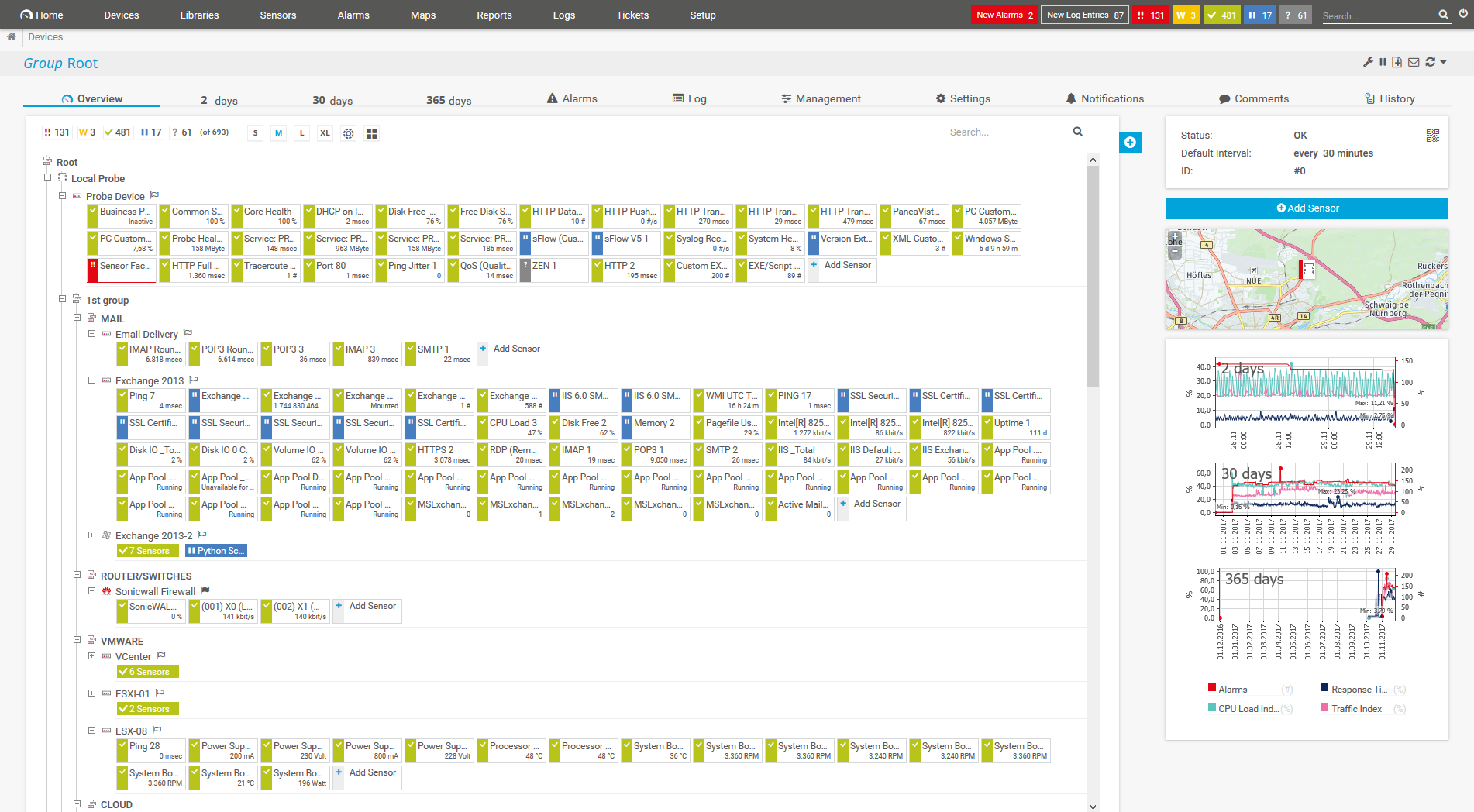
Device tree view of the complete monitoring setup
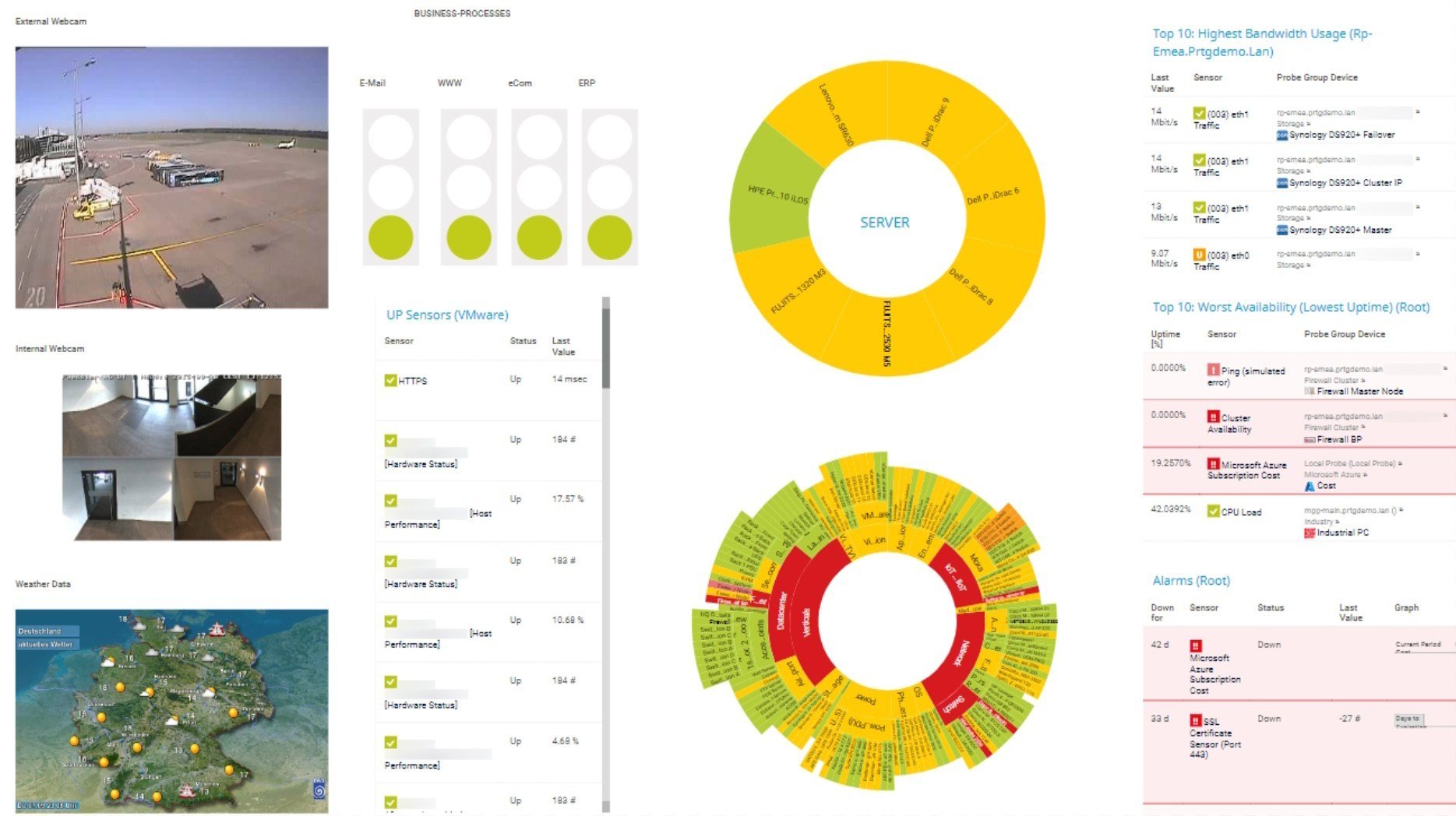
Custom PRTG dashboard for keeping an eye on the entire IT infrastructure
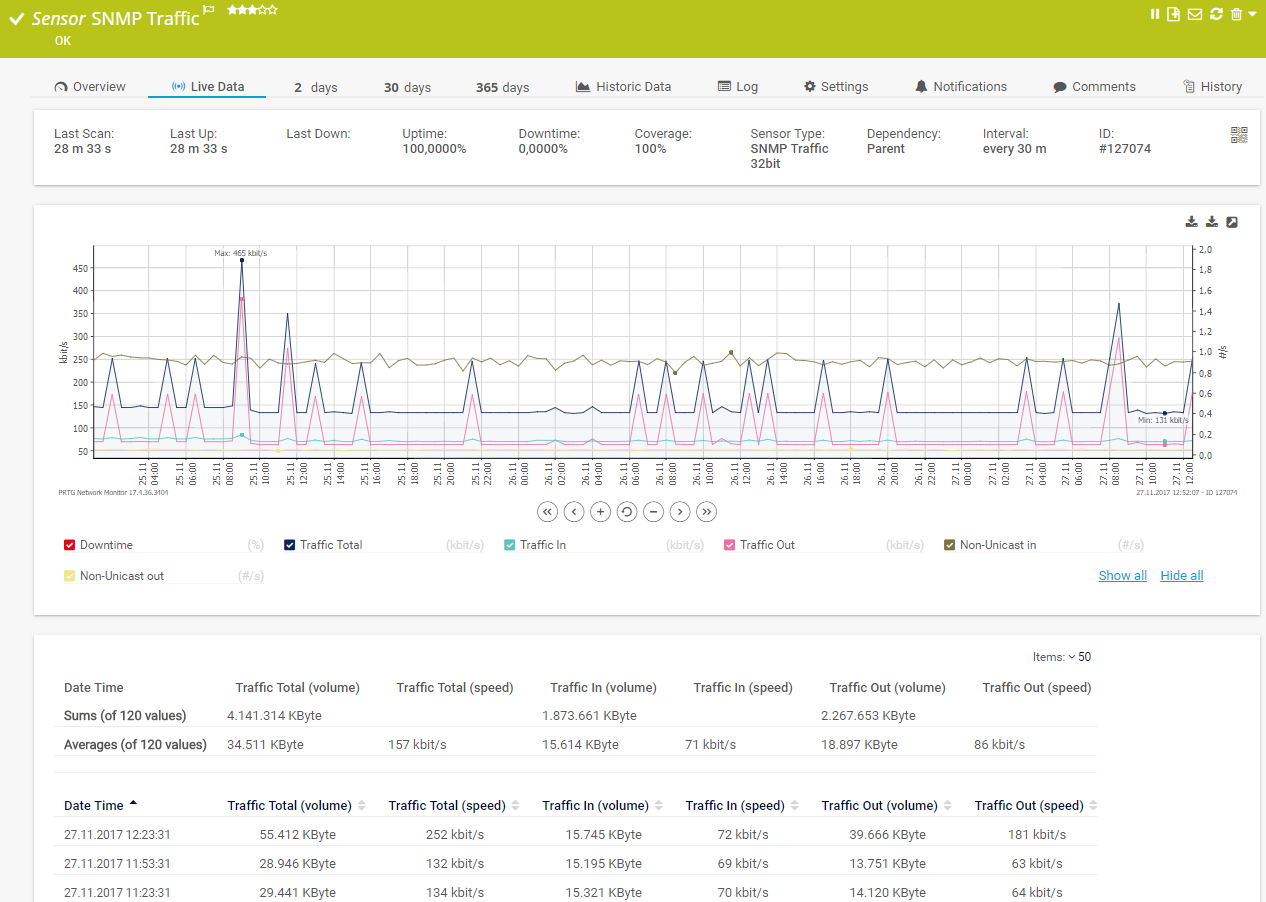
Live traffic data graph in PRTG
PRTG safeguards the integrity of every mission-critical file on your network using sophisticated sensors:
PRTG also comes with robust access management rights functionality built-in, giving you complete control over who can access and modify system files, as well as backup monitoring, so you can undo accidental or unauthorized file changes in a few clicks.
PRTG comes with more than 250 native sensor types for monitoring your entire on-premises, cloud, and hybrid cloud environment out of the box. Check out some examples below!
See the PRTG Manual for a list of all available sensor types.
Custom alerts and data visualization let you quickly identify and prevent unauthorized file changes, suspicious activity, and other potential security threats.
PRTG is set up in a matter of minutes and can be used on a wide variety of mobile devices.
“Excellent tool for detailed monitoring. Alarms and notifications work greatly. Equipment addition is straight forward and server initial setup is very easy. ...feel safe to purchase it if you intend to monitor a large networking landscape.”
Partnering with innovative IT vendors, Paessler unleashes synergies to create
new and additional benefits for joined customers.
Combining PRTG’s broad monitoring feature set with IP Fabric’s automated network assurance creates a new level of network visibility and reliability.
Paessler and Plixer provide a complete solution adding flow and metadata analysis to a powerful network monitoring tool.
With ScriptRunner Paessler integrates a powerful event automation platform into PRTG Network Monitor.
Real-time notifications mean faster troubleshooting so that you can act before more serious issues occur.
Network Monitoring Software – Version 25.3.110.1313 (August 27, 2025)
Download for Windows and cloud-based version PRTG Hosted Monitor available
English, German, Spanish, French, Portuguese, Dutch, Russian, Japanese, and Simplified Chinese
Network devices, bandwidth, servers, applications, virtual environments, remote systems, IoT, and more
Choose the PRTG Network Monitor subscription that's best for you
File integrity monitoring (FIM) identifies anomalous changes in your file automatically. It informs you when there’s suspicious activity regarding the most critical files. You can take appropriate action as soon as you get the notification so that you stay compliant.
FIM software works as a supporting tool in an incident response and prevention infrastructure and can help safeguard your system from unwanted threats, breaches, and data modifications.
Numerous industry compliance standards also recognize how important FIM security is. Many compliance organizations require you to have a comprehensive mechanism in place to secure sensitive data and demonstrate how you can maintain a secure environment.
If your organization operates in a regulated industry like financial services or health care, or services individuals in the EU and, so, is subject to GDPR, a file integrity monitoring solution makes it easier to prove to regulators you're complying with the applicable rules, because it's tangible evidence that you're tracking system files and keeping a close eye on who can access them and any changes. With PRTG, you can also create custom reports (for both regulators and auditors) with a few clicks.
But it's worth using a file integrity monitoring tool even if you're none of the above. Bad actors are continuously adapting, using increasingly sophisticated techniques to gain access to organizations' networks and the sensitive data they hold.
A FIM tool like PRTG alerts you as soon as there's activity that seems like it could be a cyberattack. And, having access to robust threat intelligence means you’ll have a safer network and safer customer data (and a lower risk of PR disasters).
PRTG is a file integrity monitoring solution that tracks, evaluates, and reports every modification to the files stored on your system. Think of it as CCTV for the critical files that keep your network – and your organization – running smoothly. Available for Windows-based on-premises servers or as a cloud-hosted solution, it's capable of monitoring unlimited local, remote, and virtual devices round the clock, so you can identify unintended or suspicious changes, and pinpoint and neutralize potential data breaches and other cybersecurity threats such as malware more quickly.
First, define a policy. Which files on your system do you want to monitor, and where are they stored?
Second, establish a baseline. That is, a definitive version of each file which the file integrity monitoring system will use to detect changes.
Third, monitor the files. With PRTG, this is as simple as assigning sensors to your endpoints and letting them do the work. You can either set it to calculate a checksum on files’ properties, or compare the live file to a backup. To minimize the risk of false positives, you can promote expected changes ahead of time. PRTG also sends you automatic in-app, text, or email notifications if there are any unauthorized or unexpected changes.
Need to prove you’re meeting the compliance requirements of PCI DSS, HIPAA, GDPR, or other industry regulations or standards? The final step is to generate reports of your monitoring activity.
Yes, you can. Set up remote probes close to the endpoints of the folders, databases, or other file systems you want to monitor. PRTG will gather the data and send it to your core server so you can see everything at a glance.
Yes. PRTG can keep an eye on hosts, bootloader, profiles, cron jobs, run comments, kernel parameters, and services and daemons in Linux and other Unix-based operating systems. You can do this either via SMB or SSH secure shell.
In PRTG, “sensors” are the basic monitoring elements. One sensor usually monitors one measured value in your network, for example the traffic of a switch port, the CPU load of a server, or the free space on a disk drive. On average, you need about 5-10 sensors per device or one sensor per switch port.
Paessler conducted trials in over 600 IT departments worldwide to tune its network monitoring software closer to the needs of sysadmins. The result of the survey: over 95% of the participants would recommend PRTG – or already have.
Paessler PRTG is used by companies of all sizes. Sysadmins love PRTG because it makes their job a whole lot easier.
Bandwidth, servers, virtual environments, websites, VoIP services – PRTG keeps an eye on your entire network.
Everyone has different monitoring needs. That’s why we let you try PRTG for free.