PRTG Manual: Add a Device
There are several ways to manually add a device:
- Select Devices | Add Device from the main menu bar. A dialog appears that guides you through the process of adding a new device.
- Hover over
 and select Add Device from the menu.
and select Add Device from the menu.
- Select Add Device from the context menu of the group to which you want to add the new device. This skips step 1 and leads you directly to step 2.
This documentation refers to an administrator that accesses the PRTG web interface on a master node. Other user accounts, interfaces, or failover nodes might not have all of the options in the way described here. In a cluster, note that failover nodes are read-only by default.
In this section:
- Add a Device
- Step 1: Select a Parent
- Step 2: Define Device Settings
- Basic Device Settings
- Additional Device Information
- Auto-Discovery Settings
- Inherited Settings
- Credentials for Windows Systems
- Credentials for Linux/Solaris/macOS (SSH/WBEM) Systems
- Credentials for VMware/XenServer
- Credentials for SNMP Devices
- Credentials for Database Management Systems
- Credentials for AWS
- Credentials for Script Sensors
- Credentials for Cisco Meraki
- Credentials for Dell EMC
- Credentials for FortiGate
- Credentials for HPE 3PAR
- Credentials for HTTP
- Credentials for Microsoft Azure
- Credentials for MQTT
- Credentials for NATS
- Credentials for NetApp
- Credentials for OPC UA
- Credentials for Soffico Orchestra
- Credentials for Proxmox
- Credentials for PRTG Data Hub
- Credentials for Redfish
- Credentials for REST API
- Credentials for Veeam
- Connection Settings for Siemens S7
- Access Rights
The Add a Device dialog appears when you add a new device to a group. It only shows the settings that are required to create the device. Therefore, you do not see all settings in this dialog.
You can change all settings on the Settings tab of the device later. For more information, see section Device Settings.
Select the group that you want to add the new device to. Click OK.
Step 2: Define Device Settings
Setting |
Description |
|---|---|
Device Name |
Enter a name to identify the device. By default, PRTG shows this name in the device tree, as well as in alarms, logs, notifications, reports, maps, libraries, and tickets.
|
IP Version |
Select the IP protocol that PRTG uses to connect to the device:
|
IPv4 Address/DNS Name |
This setting is only visible if you select IPv4 above. Enter the IP address or Domain Name System (DNS) name for the device. Most sensors that you create on this device inherit this setting and try to connect to this address for monitoring.
|
IPv6 Address/DNS Name |
This setting is only visible if you select IPv6 above. Enter the IP address or Domain Name System (DNS) name for the device. Most sensors that you create on this device inherit this setting and try to connect to this address for monitoring.
|
Tags |
Enter one or more tags. Confirm each tag with the Spacebar key, a comma, or the Enter key. You can use tags to group objects and use tag-filtered views later on. Tags are not case-sensitive. Tags are automatically inherited.
|
Setting |
Description |
|---|---|
Device Icon |
Select a device icon. PRTG shows it in the device tree. |
Setting |
Description |
|---|---|
Auto-Discovery Level |
Select the level of detail for the auto-discovery:
|
Schedule |
Select when PRTG runs the auto-discovery:
|
Device Templates |
This setting is only visible if you select Auto-discovery with specific device templates above. Select one or more device templates by enabling a checkbox in front of the template name. PRTG uses the device templates that you select for the auto-discovery on the device:
Once the auto-discovery is finished, PRTG creates a new ticket and lists the device templates that it used to create new sensors. |
By default, all of these settings are inherited from objects that are higher in the hierarchy. We recommend that you change them centrally in the root group settings if necessary. To change a setting for this object only, click ![]() under the corresponding setting name to disable the inheritance and to display its options.
under the corresponding setting name to disable the inheritance and to display its options.
For more information, see section Inheritance of Settings.
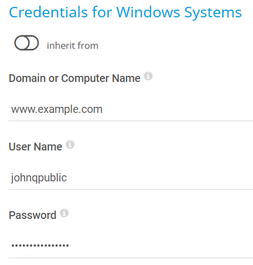
Credentials for Windows Systems
Click ![]() to interrupt the inheritance.
to interrupt the inheritance.
The settings you define in this section apply to the following sensors:
Setting |
Description |
|---|---|
Domain or Computer Name |
Enter the domain or computer name of the user account with which you want to access the Windows system. PRTG uses this account for Windows Management Instrumentation (WMI) sensors and other Windows sensors. If you want to use a Windows local user account on the target device, enter the computer name. If you want to use a Windows domain user account (recommended), enter the domain name. PRTG automatically adds a prefix to use the NT LAN Manager (NTLM) protocol if you do not explicitly define it. Do not leave this field empty. |
User Name |
Enter the user name for access to the Windows system. Usually, you use credentials with administrator rights. |
Password |
Enter the password for access to the Windows system. Usually, you use credentials with administrator rights. |
Credentials for Linux/Solaris/macOS (SSH/WBEM) Systems
Click ![]() to interrupt the inheritance.
to interrupt the inheritance.
The settings you define in this section apply to the following sensors:
- SSH Disk Free
- SSH Disk Free v2
- SSH INodes Free v2
- SSH Load Average v2
- SSH Meminfo v2
- SSH Remote Ping v2
- SSH SAN Enclosure
- SSH SAN Logical Disk
- SSH SAN Physical Disk
- SSH SAN System Health
- SSH Script
- SSH Script v2
- SSH Script Advanced
- VMware Host Hardware (WBEM)
Setting |
Description |
|---|---|
User Name |
Enter the user name for access to the Linux/Solaris/macOS system via Secure Shell (SSH) and Web-based Enterprise Management (WBEM). Usually, you use credentials with administrator rights. |
Authentication Method |
Select the authentication method for the login:
|
Password |
This setting is only visible if you select Password (default) above. Enter a password for access to the Linux/Solaris/macOS system via SSH and WBEM. Usually, you use credentials with administrator rights. |
Private Key |
This setting is only visible if you select Private key above. Paste the entire RSA private key, including the BEGIN and END lines. Make sure that a corresponding public key exists on the target device.
|
WBEM Protocol |
Select the protocol that you want to use for the connection to the system via WBEM:
|
WBEM Port |
Select if you want to use one of the default ports for the connection to the system via WBEM or if you want to set a custom port:
|
Custom WBEM Port |
This setting is only visible if you select Custom above. Enter a custom WBEM port. Enter an integer. |
SSH Port |
Enter the port for SSH connections. Enter an integer. The default port is 22.
|
SSH Rights Elevation |
Select the rights that you want to use to run the command on the target system:
|
Target System User Name |
This setting is only visible if you select an option that includes sudo or su above. Enter a user name to run the specified command on the target system as a different user than the root user. If you leave this field empty, you run the command as a root user. Make sure that you set the Linux password even if you use a public key or a private key for authentication. This is not necessary if the user is allowed to run the command without a password. |
Password |
This setting is only visible if you select an option that includes sudo or su with password above. Enter the password to run the sudo command or the su command. |
SSH Connection Mode |
Select the connection mode that you want to use to access data with SSH sensors:
|
Credentials for VMware/XenServer
Click ![]() to interrupt the inheritance.
to interrupt the inheritance.
The settings you define in this section apply to the following sensors:
- Citrix XenServer Host
- Citrix XenServer Virtual Machine
- VMware Datastore (SOAP)
- VMware Host Hardware (WBEM)
- VMware Host Hardware Status (SOAP)
- VMware Host Performance (SOAP)
- VMware Virtual Machine (SOAP)
Setting |
Description |
|---|---|
User Name |
Enter the user name for access to VMware ESXi, vCenter Server, or Citrix XenServer. Usually, you use credentials with administrator rights. |
Password |
Enter the password for access to VMware ESXi, vCenter Server, or Citrix XenServer. Usually, you use credentials with administrator rights.
|
VMware Protocol |
Select the protocol for the connection to VMware ESXi, vCenter Server, or Citrix XenServer:
|
Session Handling |
Select if you want to reuse a session for VMware sensors:
|
Click ![]() to interrupt the inheritance.
to interrupt the inheritance.
The settings you define in this section apply to the following sensors:
Setting |
Description |
|---|---|
SNMP Version |
Select the Simple Network Management Protocol (SNMP) version for the connection to the target SNMP device:
|
Community String |
This setting is only visible if you select SNMP v1 or SNMP v2c (default) above. Enter the community string of your device. This is like a clear-text password for simple authentication.
|
Authentication Method |
This setting is only visible if you select SNMP v3 above. Select the authentication method:
|
User Name |
This setting is only visible if you select SNMP v3 above. Enter the user name for access to the target SNMP device.
|
Password |
This setting is only visible if you select SNMP v3 above. Enter the password for access to the target SNMP device.
|
Encryption Type |
This setting is only visible if you select SNMP v3 above. Select an encryption type:
|
Encryption Key |
This setting is only visible if you select SNMP v3 above. Enter an encryption key. If you provide a key, PRTG encrypts SNMP data packets with the encryption algorithm that you selected above. Enter a string or leave the field empty.
|
Context Name |
This setting is only visible if you select SNMP v3 above. Enter a context name only if the configuration of the device requires it. Context is a collection of management information that is accessible by an SNMP device. Enter a string. |
SNMP Port |
Enter the port for the connection to the SNMP target device. Enter an integer. The default port is 161.
|
Timeout (Sec.) |
Enter a timeout in seconds for the request. Enter an integer. The maximum timeout value is 300 seconds (5 minutes). |
Credentials for Database Management Systems
Click ![]() to interrupt the inheritance.
to interrupt the inheritance.
The settings you define in this section apply to the following sensors:
Setting |
Description |
|---|---|
Port |
Select the port that PRTG uses for connections to the monitored databases:
|
Custom Port |
Enter a custom port for database connections. Enter an integer.
|
Authentication Method |
Select the authentication method for the connection to the Structured Query Language (SQL) database:
|
User Name |
This setting is only visible if you select SQL server authentication above. Enter the user name for the database connection. |
Password |
This setting is only visible if you select SQL server authentication above. Enter the password for the database connection. |
Timeout (Sec.) |
Enter a timeout in seconds for the request. Enter an integer. The maximum timeout value is 900 seconds (15 minutes). |
Click ![]() to interrupt the inheritance.
to interrupt the inheritance.
The settings you define in this section apply to the following sensors:
For more information about the permissions that are necessary to query the AWS API, see the Knowledge Base: How do I set permissions for the Amazon Web Services (AWS) API key to use certain sensors in PRTG?
Setting |
Description |
|---|---|
Access Key |
Enter the Amazon Web Services (AWS) access key. |
Secret Key |
Enter the AWS secret key. |
Credentials for Script Sensors
Click ![]() to interrupt the inheritance.
to interrupt the inheritance.
The settings you define in this section apply to the following sensors:
Setting |
Description |
|---|---|
Placeholder 1 Description |
Enter a description for Placeholder 1, for example information about the purpose or content of the placeholder. |
Placeholder 1 |
Enter a value for the placeholder. PRTG inserts the value for the script execution if you add %scriptplaceholder1 in the argument list. PRTG does not display the value in the sensor log or the sensor's settings. |
Placeholder 2 Description |
Enter a description for Placeholder 2, for example information about the purpose or content of the placeholder. |
Placeholder 2 |
Enter a value for the placeholder. PRTG inserts the value for the script execution if you add %scriptplaceholder2 in the argument list. PRTG does not display the value in the sensor log or the sensor's settings. |
Placeholder 3 Description |
Enter a description for Placeholder 3, for example information about the purpose or content of the placeholder. |
Placeholder 3 |
Enter a value for the placeholder. PRTG inserts the value for the script execution if you add %scriptplaceholder3 in the argument list. PRTG does not display the value in the sensor log or the sensor's settings. |
Placeholder 4 Description |
Enter a description for Placeholder 4, for example information about the purpose or content of the placeholder. |
Placeholder 4 |
Enter a value for the placeholder. PRTG inserts the value for the script execution if you add %scriptplaceholder4 in the argument list. PRTG does not display the value in the sensor log or the sensor's settings. |
Placeholder 5 Description |
Enter a description for Placeholder 5, for example information about the purpose or content of the placeholder. |
Placeholder 5 |
Enter a value for the placeholder. PRTG inserts the value for the script execution if you add %scriptplaceholder5 in the argument list. PRTG does not display the value in the sensor log or the sensor's settings. |
Click ![]() to interrupt the inheritance.
to interrupt the inheritance.
The settings you define in this section apply to the following sensors:
Setting |
Description |
|---|---|
API Key |
Enter an API key that the sensor uses for authentication against the Cisco Meraki Dashboard API. |
Meraki Dashboard API Endpoint |
Enter the endpoint for the Cisco Meraki Dashboard API. The default api.meraki.com should be valid for most use cases.
|
Click ![]() to interrupt the inheritance.
to interrupt the inheritance.
The settings you define in this section apply to the following sensors:
- Dell EMC Unity Enclosure Health v2
- Dell EMC Unity File System v2
- Dell EMC Unity Storage Capacity v2
- Dell EMC Unity Storage LUN v2
- Dell EMC Unity Storage Pool v2
- Dell EMC Unity VMware Datastore v2
Setting |
Description |
|---|---|
User Name |
Enter the user name for access to the Dell EMC system. |
Password |
Enter the password for access to the Dell EMC system. |
Port |
Enter the port for the connection to the Dell EMC system. The default port for secure connections is 443. |
Click ![]() to interrupt the inheritance.
to interrupt the inheritance.
The settings you define in this section apply to the following sensors:
Setting |
Description |
|---|---|
API Token |
Enter the API token for access to the FortiGate system. |
Port |
Enter the port for the connection to the FortiGate system. The default port for secure connections is 443. |
Click ![]() to interrupt the inheritance.
to interrupt the inheritance.
The settings you define in this section apply to the following sensors:
Setting |
Description |
|---|---|
User Name |
Enter the user name for access to the HPE 3PAR system. |
Password |
Enter the password for access to the HPE 3PAR system. |
Protocol |
Select the protocol that you want to use for the connection to the HPE 3PAR system:
|
WSAPI Port |
Enter the Web Services API (WSAPI) port for the connection to the HPE 3PAR system. The default port for secure connections is 8080 and the default port for unsecure connections is 8008.
|
SSH Port |
Enter the SSH port for the connection to the HPE 3PAR system. The default port for secure connections is 22. |
Click ![]() to interrupt the inheritance.
to interrupt the inheritance.
The settings you define in this section apply to the following sensor:
Setting |
Description |
|---|---|
Authentication Method |
Select the authentication method for access to the server:
|
User Name |
This setting is only visible if you select Basic authentication above. Enter the user name for access to the server. |
Password |
This setting is only visible if you select Basic authentication above. Enter the password for access to the server. |
Bearer Token |
This setting is only visible if you select Bearer authentication above. Enter a bearer token for access to the server. |
Placeholder 1 Description |
Enter a description for Placeholder 1, for example information about the purpose or content of the placeholder. |
Placeholder 1 |
Enter a value for the placeholder. PRTG inserts the value for the HTTP request if you add %httpplaceholder1 in the URL, POST Body, and Custom Headers fields of the HTTP v2 sensor. PRTG does not display the value in the sensor log or the sensor's settings. |
Placeholder 2 Description |
Enter a description for Placeholder 2, for example information about the purpose or content of the placeholder. |
Placeholder 2 |
Enter a value for the placeholder. PRTG inserts the value for the HTTP request if you add %httpplaceholder2 in the URL, POST Body, and Custom Headers fields of the HTTP v2 sensor. PRTG does not display the value in the sensor log or the sensor's settings. |
Placeholder 3 Description |
Enter a description for Placeholder 3, for example information about the purpose or content of the placeholder. |
Placeholder 3 |
Enter a value for the placeholder. PRTG inserts the value for the HTTP request if you add %httpplaceholder3 in the URL, POST Body, and Custom Headers fields of the HTTP v2 sensor. PRTG does not display the value in the sensor log or the sensor's settings. |
Placeholder 4 Description |
Enter a description for Placeholder 4, for example information about the purpose or content of the placeholder. |
Placeholder 4 |
Enter a value for the placeholder. PRTG inserts the value for the HTTP request if you add %httpplaceholder4 in the URL, POST Body, and Custom Headers fields of the HTTP v2 sensor. PRTG does not display the value in the sensor log or the sensor's settings. |
Placeholder 5 Description |
Enter a description for Placeholder 5, for example information about the purpose or content of the placeholder. |
Placeholder 5 |
Enter a value for the placeholder. PRTG inserts the value for the HTTP request if you add %httpplaceholder5 in the URL, POST Body, and Custom Headers fields of the HTTP v2 sensor. PRTG does not display the value in the sensor log or the sensor's settings. |
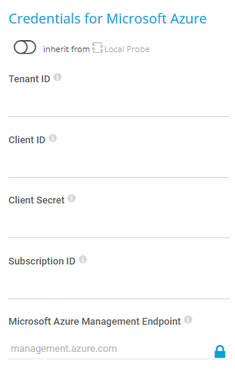
Credentials for Microsoft Azure
The settings you define in this section apply to the following sensors:
- Microsoft Azure SQL Database
- Microsoft Azure Storage Account
- Microsoft Azure Subscription Cost
- Microsoft Azure Virtual Machine
The sensors use the credentials to authenticate with Microsoft Entra ID.
For more information about the credentials and permissions that are necessary use the Microsoft Azure sensors, see the Knowledge Base: How do I obtain credentials and create custom roles for the Microsoft Azure sensors?
Setting |
Description |
|---|---|
Tenant ID |
Enter the Microsoft Entra tenant ID.
|
Client ID |
Enter the Microsoft Entra client ID. |
Client Secret |
Enter the Microsoft Entra client secret. |
Subscription ID |
Enter the Microsoft Entra subscription ID. |
Click ![]() to interrupt the inheritance.
to interrupt the inheritance.
The settings you define in this section apply to the following sensors:
Setting |
Description |
|---|---|
Authentication Method |
Select if you want to connect without credentials or define credentials for access to the MQTT broker:
|
User Name |
This setting is only visible if you select User name and password above. Enter the user name for access to the Message Queue Telemetry Transport (MQTT) broker. |
Password |
This setting is only visible if you select User name and password above. Enter the password for access to the MQTT broker. |
Port |
Enter the port for the connection to the MQTT broker. The default port for secure connections is 8883 and the default port for unsecure connections is 1883. |
Transport-Level Security |
Select if you want to use a Secure Sockets Layer (SSL)/Transport Layer Security (TLS) secured connection:
|
Server Authentication |
This setting is only visible if you select Use transport-level security above. Select if you want to use a certificate for server authentication:
|
CA Certificate |
This setting is only visible if you select Enable above. Enter the certificate authority (CA) certificate for the verification of the MQTT broker.
|
Client Authentication |
This setting is only visible if you select Use transport-level security above. Select if you want to use a certificate for client authentication:
|
Client Certificate |
This setting is only visible if you select Enable above. Enter the certificate that you created for authenticating the sensor against the MQTT broker.
|
Client Key |
This setting is only visible if you select Enable above. Enter the client key for access to the MQTT broker.
|
Client Key Password |
This setting is only visible if you select Enable above. Enter the password for the client key. |
Click ![]() to interrupt the inheritance.
to interrupt the inheritance.
The settings you define in this section apply to the following sensor:
Setting |
Description |
|---|---|
Connection Security |
Select if you want to use an encrypted Transport Layer Security (TLS) connection to the NATS server:
|
TLS-First Handshake |
This setting is only visible if you select Use TLS (default) above. Specify if the sensor connects to the NATS server using a TLS-first handshake:
|
Authentication Method |
Select how PRTG authenticates against the NATS server:
|
User Name |
This setting is only visible if you select User name and password (default) above. Enter a user name for access to the NATS server. |
Password |
This setting is only visible if you select User name and password (default) above. Enter the password for access to the NATS server. |
User NKey |
This setting is only visible if you select NKey above. Enter the user NKey to authenticate against the NATS server. The user NKey is prefixed with a U. |
Seed NKey |
This setting is only visible if you select NKey above. Enter the seed NKey to authenticate against the NATS server. The seed NKey is prefixed with an S. |
NATS Credentials |
This setting is only visible if you select NATS Credentials above. Enter the NATS credentials in the NATS credentials file format to authenticate against the NATS server. |
Port |
Enter the port for the connection to the NATS server. The default port is 4222. |
Click ![]() to interrupt the inheritance.
to interrupt the inheritance.
The settings you define in this section apply to the following sensors:
- NetApp Aggregate v2
- NetApp I/O v2
- NetApp LIF v2
- NetApp LUN v2
- NetApp NIC v2
- NetApp Physical Disk v2
- NetApp SnapMirror v2
- NetApp System Health v2
- NetApp Volume v2
The sensors use the credentials for access to the ONTAP System Manager.
Setting |
Description |
|---|---|
User Name |
Enter a user name for access to the ONTAP System Manager. |
Password |
Enter the password for access to the ONTAP System Manager. |
Port |
Enter the port for the connection to the ONTAP System Manager. The default port for secure connections is 443. |
Protocol |
Select the protocol that you want to use for the connection to the ONTAP System Manager:
|
Click ![]() to interrupt the inheritance.
to interrupt the inheritance.
The settings you define in this section apply to the following sensors:
Setting |
Description |
|---|---|
Port |
Enter the port for the connection to the OPC Unified Architecture (OPC UA) server. The default port for secure connections is 4840. |
Server Path |
Enter the path of the OPC UA server endpoint if you run more than one server under the same IP address or DNS name. |
Security Mode |
Select if you want to use encryption:
|
Security Policy |
This setting is only visible if you select Sign or Sign & Encrypt above. Select if you want to use a security policy and define which policy you want to use:
|
Client Certificate |
This setting is only visible if you select Sign or Sign & Encrypt above. Enter the certificate that you created for authenticating the sensor against the OPC UA server.
|
Client Key |
This setting is only visible if you select Sign or Sign & Encrypt above. Enter the client key for access to the OPC UA server.
|
Client Key Password |
This setting is only visible if you select Sign or Sign & Encrypt above. Enter the password for the client key. |
Select if you want to connect without credentials or define credentials for access to the OPC UA server:
|
|
User Name |
This setting is only visible if you select User name and password above. Enter the user name for access to the OPC UA server. |
Password |
This setting is only visible if you select User name and password above. Enter the password for access to the OPC UA server. |
Credentials for Soffico Orchestra
Click ![]() to interrupt the inheritance.
to interrupt the inheritance.
The settings you define in this section apply to the following sensor:
Setting |
Description |
|---|---|
Authentication Method |
Select if you want to connect without credentials or define credentials for access to the Orchestra platform:
|
User Name |
This setting is only visible if you select User name and password above. Enter the user name for access to the Orchestra platform. |
Password |
This setting is only visible if you select User name and password above. Enter the password for access to the Orchestra platform. |
Timeout (Sec.) |
Enter a timeout in seconds for the request. Enter an integer. The maximum timeout value is 300 seconds (5 minutes). |
Port |
Enter the port for the connection to the Orchestra platform. The default port for secure connections is 8443 and the default port for unsecure connections is 8019. |
Protocol |
Select the protocol that you want to use for the connection to the Orchestra platform:
|
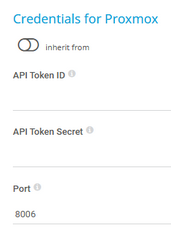
Click ![]() to interrupt the inheritance.
to interrupt the inheritance.
The settings you define in this section apply to the following sensors:
Setting |
Description |
|---|---|
API Token ID |
Enter the full API token ID for authentication of the Proxmox Virtual Environment (Proxmox VE) API in the format user@realm!tokenID.
|
API Token Secret |
Enter the UUID secret of the Proxmox VE API token. |
Port |
Enter the port for the connection to the Proxmox VE virtual machine. The default port is 8006. PRTG supports ports 1-65535. |
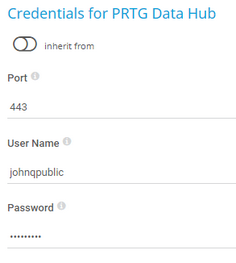
Click ![]() to interrupt the inheritance.
to interrupt the inheritance.
The settings you define in this section apply to the following sensors:
Setting |
Description |
|---|---|
Port |
Enter the port for the metrics endpoint of the PRTG Data Hub API. The default port is 443. |
User Name |
Enter the user name for access to the PRTG Data Hub API. |
Password |
Enter the password for access to the PRTG Data Hub API. |
Click ![]() to interrupt the inheritance.
to interrupt the inheritance.
The settings you define in this section apply to the following sensors:
Setting |
Description |
|---|---|
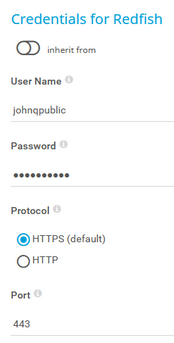
User Name |
Enter the user name for access to the Redfish system. |
Password |
Enter the password for access to the Redfish system. |
Protocol |
Select the protocol that you want to use for the connection to the Redfish system:
|
Port |
Enter the port for the connection to the Redfish system. The default port for secure connections is 443. |
Click ![]() to interrupt the inheritance.
to interrupt the inheritance.
The settings you define in this section apply to the following sensor:
Setting |
Description |
|---|---|
Authentication Method |
Select the authentication method for access to the Representational State Transfer (REST) application programming interface (API):
|
User Name |
This setting is only visible if you select Basic authentication above. Enter the user name for access to the REST API. |
Password |
This setting is only visible if you select Basic authentication above. Enter the password for access to the REST API. |
Bearer Token |
This setting is only visible if you select Bearer authentication above. Enter a bearer token for access to the REST API. |
Login Path |
This setting is only visible if you select Session-based authentication above. Enter a URL for the login request that uses GET or POST, for example, /api/login. You can optionally add a specific port number to the request, for example, https://:443/api/login. |
Authentication Header |
This setting is only visible if you select Session-based authentication above. Select whether to include an authentication header in the login request:
|
Login Request Method |
This setting is only visible if you select Session-based authentication above. Select the method for the login request:
|
POST Data |
This setting is only visible if you select Session-based authentication and POST above. Enter the data to POST to the login path. You can use placeholders, for example, %restusername or %restpassword. |
Custom Headers |
This setting is only visible if you select Session-based authentication above. Enter any custom headers. Enter one header per line. |
Login Result Type |
This setting is only visible if you select Session-based authentication above. Select the type of the login result.
|
Login Header Name |
This setting is only visible if you select Session-based authentication and Header (default) above. Enter the header name to get the session key value in the login response. For example, X-Authenticate. This setting is case-sensitive. |
Login Cookie Name |
This setting is only visible if you select Session-based authentication and Cookie above. Enter the cookie name to get the session key value in the login response. For example, X-Authenticate. This setting is case-sensitive. |
JSONPath |
This setting is only visible if you select Session-based authentication and JSON above. Enter the JSONPath to the session key value in the login response. For example, $["X-Authenticate"]. This setting is case-sensitive. |
XPath |
This setting is only visible if you select Session-based authentication and XML above. Enter the XML path (XPath) to the session key value in the login response. For example, /root/X-Authenticate/text(). This setting is case-sensitive. |
Token Type |
This setting is only visible if you select Session-based authentication above. Select the token type to use for authorization:
|
Header Name |
This setting is only visible if you select Session-based authentication and Via header above. Enter the header name to use for authorization. For example, X-Authenticate. This setting is case-sensitive. |
Cookie Name |
This setting is only visible if you select Session-based authentication and Via cookie above. Enter the cookie name to use for authorization. For example, X-Authenticate. This setting is case-sensitive. |
Placeholder 1 |
Enter a value for the placeholder. PRTG inserts the value for the REST API request if you add %restplaceholder1 in the Request URL, POST Body, and Custom Headers fields of the REST Custom v2 sensor. PRTG does not display the value in the sensor log or the sensor's settings. |
Placeholder 2 Description |
Enter a description for Placeholder 2, for example information about the purpose or content of the placeholder. |
Placeholder 2 |
Enter a value for the placeholder. PRTG inserts the value for the REST API request if you add %restplaceholder2 in the Request URL, POST Body, and Custom Headers fields of the REST Custom v2 sensor. PRTG does not display the value in the sensor log or the sensor's settings. |
Placeholder 3 Description |
Enter a description for Placeholder 3, for example information about the purpose or content of the placeholder. |
Placeholder 3 |
Enter a value for the placeholder. PRTG inserts the value for the REST API request if you add %restplaceholder3 in the Request URL, POST Body, and Custom Headers fields of the REST Custom v2 sensor. PRTG does not display the value in the sensor log or the sensor's settings. |
Placeholder 4 Description |
Enter a description for Placeholder 4, for example information about the purpose or content of the placeholder. |
Placeholder 4 |
Enter a value for the placeholder. PRTG inserts the value for the REST API request if you add %restplaceholder4 in the Request URL, POST Body, and Custom Headers fields of the REST Custom v2 sensor. PRTG does not display the value in the sensor log or the sensor's settings. |
Placeholder 5 Description |
Enter a description for Placeholder 5, for example information about the purpose or content of the placeholder. |
Placeholder 5 |
Enter a value for the placeholder. PRTG inserts the value for the REST API request if you add %restplaceholder5 in the Request URL, POST Body, and Custom Headers fields of the REST Custom v2 sensor. PRTG does not display the value in the sensor log or the sensor's settings. |
Click ![]() to interrupt the inheritance.
to interrupt the inheritance.
The settings you define in this section apply to the following sensors:
Setting |
Description |
|---|---|
User Name |
Enter the user name for access to the Veeam Backup Enterprise Manager. |
Password |
Enter the password for access to the Veeam Backup Enterprise Manager. |
Port |
Enter the port for the connection to the Veeam Backup Enterprise Manager. The default port for secure connections is 9398. |
Connection Settings for Siemens S7
Click ![]() to interrupt the inheritance.
to interrupt the inheritance.
The settings you define in this section apply to the following sensors:
Setting |
Description |
|---|---|
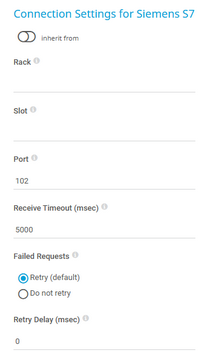
Rack |
Enter the rack number of the CPU that this sensor monitors. You can define a rack from 0 to 7. |
Slot |
Enter the slot number of the CPU that this sensor monitors. You can define a slot from 0 to 31. |
Port |
Enter the port for the S7 protocol. The default port is 102. |
Receive Timeout (msec) |
Enter a receive timeout in milliseconds (msec). If the reply from the device takes longer than this value, PRTG aborts the request and triggers an error message. The default is 5000 msec (5 seconds). |
Failed Requests |
Select if PRTG tries again after a request fails:
|
Retry Delay (msec) |
Enter the time in msec that PRTG waits before it sends another READ request when a request fails. The default delay is 0 msec. You can define a delay between 0 and 100. |
Click ![]() to interrupt the inheritance.
to interrupt the inheritance.
Setting |
Description |
|---|---|
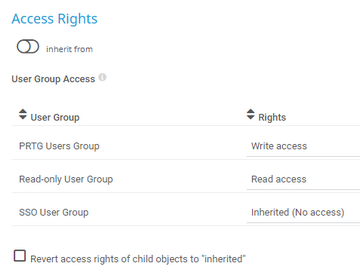
User Group Access |
Select the user groups that have access to the object. You see a table with user groups and group access rights. The table contains all user groups in your setup. For each user group, you can choose from the following group access rights:
To automatically set all child objects to inherit this object's access rights, select the Revert access rights of child objects to "inherited" option.
|
Click OK to save your settings. If you close the dialog without saving, all changes to the settings are lost.
KNOWLEDGE BASE
What security features does PRTG include?