Custom alerts and data visualization let you quickly identify and prevent cyber security and data breach issues.
Companies have never been as vulnerable to network attacks as they are today. Hackers operate globally and generate income across the Internet.
Companies have come to realize that as their virtual presence grows, so does the number of gateways in their networks. These interfaces are used by hackers in an increasingly sophisticated manner, creating a problem that only gets worse as a company’s IT infrastructure becomes more complex.
Network attacks can damage your company in serious ways:
Comprehensive network monitoring tools such as Paessler PRTG are vital for maintaining the security of your network – for what good does a firewall do that’s not available, or backup software that malfunctions?
With network monitoring software, you can keep a constant eye on security components, antivirus software, and backups, and automatically be warned in the event of trouble.
Network traffic analysis, which is included in PRTG, lets you monitor and check data traffic for suspicious behavior such as unusually high traffic loads.
It also helps you determine which data and systems are affected by network attacks that already happened. By evaluating historical data records, you can not only prevent cybersecurity issues like DDoS attacks, but also significantly reduce downtime.
Diagnose network issues by continuously tracking the security of your entire network. Show unauthorized access, unusual network traffic, data breaches, unavailable firewalls, or malfunctioning antivirus software in real time. Visualize monitoring data in clear graphs and dashboards to identify problems more easily. Gain the overview you need to troubleshoot weak spots in your IT infrastructure that can present a security threat.
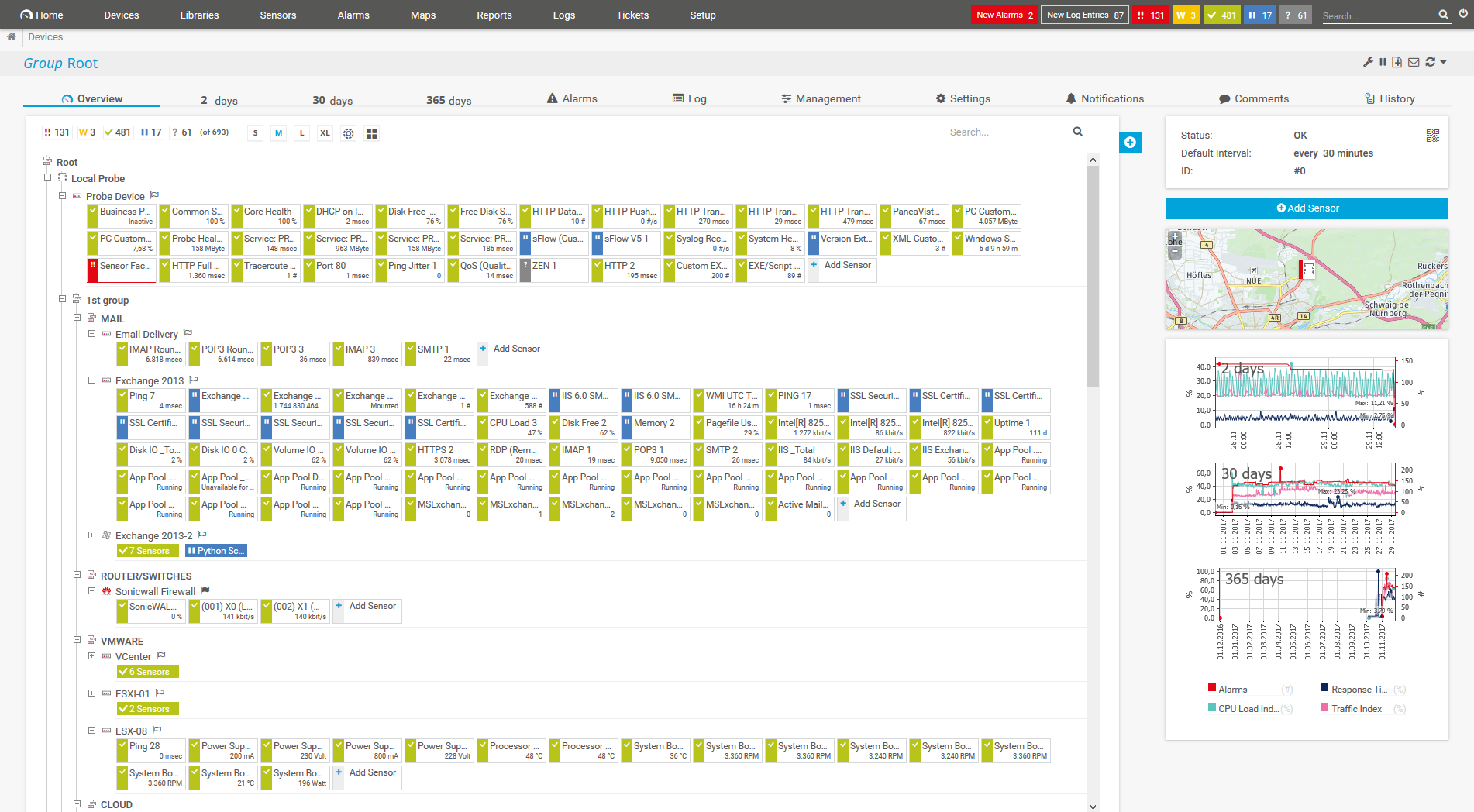
Device tree view of the complete monitoring setup
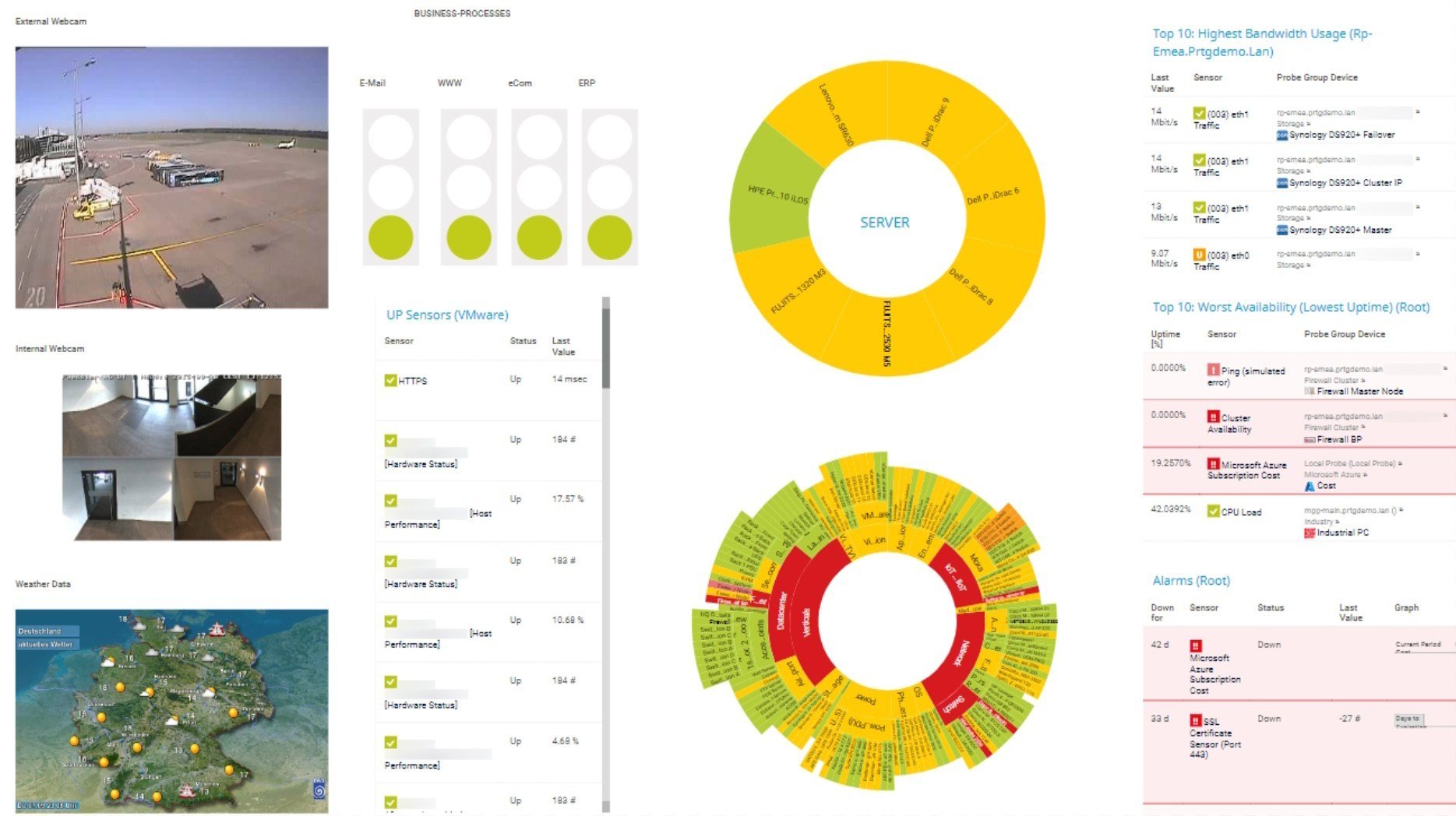
Custom PRTG dashboard for keeping an eye on the entire IT infrastructure
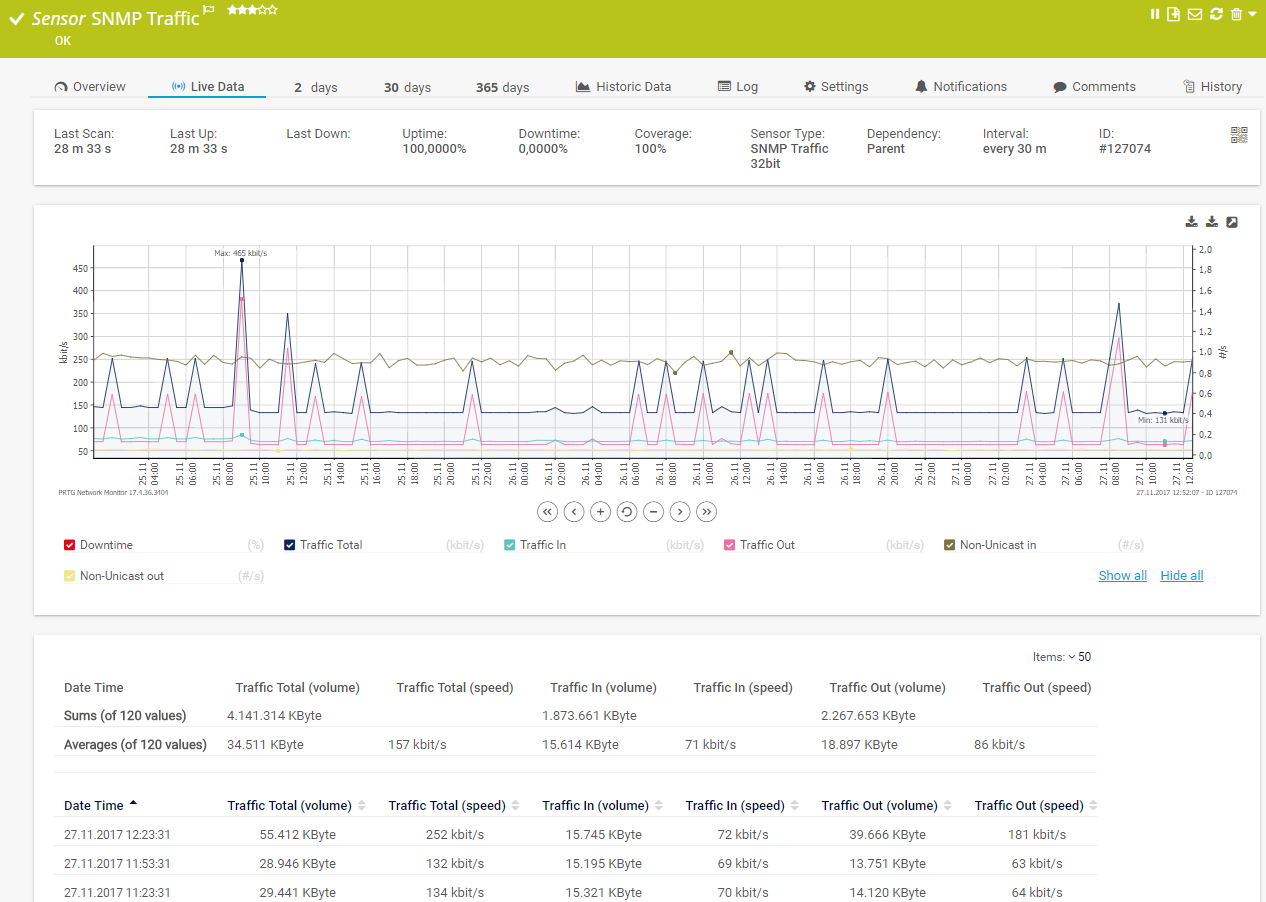
Live traffic data graph in PRTG
PRTG comes with more than 250 native sensor types for monitoring your entire on-premises, cloud, and hybrid cloud environment out of the box. Check out some examples below!
See the PRTG Manual for a list of all available sensor types.
Custom alerts and data visualization let you quickly identify and prevent cyber security and data breach issues.
PRTG is set up in a matter of minutes and can be used on a wide variety of mobile devices.
Partnering with innovative IT vendors, Paessler unleashes synergies to create
new and additional benefits for joined customers.
Combining PRTG’s broad monitoring feature set with IP Fabric’s automated network assurance creates a new level of network visibility and reliability.
Combine PRTG’s monitoring of everything with SQmediator’s deep insights into your communications infrastructure to ensure and improve your company’s communications plant and troubleshooting abilities.
Axis offers one of the most complete and reliable product portfolios, an expanded professional network, and comprehensive integration support for video management software.
Real-time notifications mean faster troubleshooting so that you can act before more serious issues occur.
Network Monitoring Software – Version 25.3.110.1313 (August 27, 2025)
Download for Windows and cloud-based version PRTG Hosted Monitor available
English, German, Spanish, French, Portuguese, Dutch, Russian, Japanese, and Simplified Chinese
Network devices, bandwidth, servers, applications, virtual environments, remote systems, IoT, and more
Choose the PRTG Network Monitor subscription that's best for you
Network attack monitoring is the process of continuously observing and analyzing network activity to detect, respond to, and prevent malicious activities or security breaches.
It involves the use of various tools, techniques, and practices to ensure that any unauthorized or suspicious actions within a network are identified and mitigated immediately, for example:
Network attacks can be categorized in various ways based on their objectives, techniques, and targets. Here's an overview of the major types of network attacks:
1. Denial of Service (DoS) and Distributed Denial of Service (DDoS) attacks
2. Man-in-the-Middle (MitM) attacks
3. Phishing and spear phishing attacks
4. SQL injection attacks
Exploiting vulnerabilities in an application's software by injecting malicious SQL queries to manipulate the database.
5. Cross-Site Scripting (XSS)
Injecting malicious scripts into web pages viewed by other users. These scripts can steal data, hijack user sessions, or perform unauthorized actions.
6. Malware attacks
7. Credential-based attacks
8. Insider threats
Attacks originating from within the organization by trusted individuals who misuse their access rights.
9. Exploiting unpatched vulnerabilities
Taking advantage of known vulnerabilities in software or hardware that have not been patched or updated.
10. Network sniffing and spoofing
The best way to prevent network attacks is by reducing the number of weak spots in your network. Weak spots not only include software flaws, runtime errors, and complex IT infrastructures, but also careless employees.
Address software flaws
Always assume software is faulty, and that bugs will create gateways. Exploits use weak spots to gain access to external computers and install malware. These exploits are saved in “exploit kits” and sold to interested parties with convenient user interfaces. If you discover a weak spot and see that a patch or update is available, install the fix quickly–preferably with an automated update distributor that covers all the workstations in your company.
View IT security as an ongoing process
Technology never stops evolving, with software offering more and more new functions and security loopholes popping up endlessly. When new security software is released, there is already a hacker who knows how to crack it. This means you must view IT security as an ongoing task that never ends.
Set up comprehensive security measures
A comprehensive approach that goes beyond virus scanners and firewalls is vital to network security. IT security has expanded to include updates, training sessions, monitoring, intelligent security tools, and even collaboration with other companies in your sector to address current developments surrounding IT security issues.
Reduce IT complexity
The more complex your infrastructure, the more vulnerable your system. Simplify IT structures and minimize the number of tools you use to help ward off potential attacks. All software creates gateways, either itself or when run with other programs. By keeping things simple, you close off potential gateways and prevent hackers from finding a way inside.
Put IT security at the forefront
IT security should be a major consideration with any new project – and not just for those in charge of security and data protection. IT administrators and software developers must also be up to speed. And while management may pass on specific tasks, they should likewise stay informed of all security developments.
Stick to “state-of-the-art” technology
The law requires that companies use “state-of-the-art” technology, but allows for exceptions in certain situations. Companies must stay up-to-date on all technological developments. However, because the provisions are quite vague and spread out amongst several different regulations, it is recommended that you formulate a strategy with the advice of a legal professional.
Get employees on the same page
Employee training should be part of your security model. Your biggest challenge will be to entice employees who have little interest in IT security. Because your task is ongoing, proactive employee training should be an essential part of your approach.
Make it costly for hackers
Professional hackers have expenses and seek to make profits. They’re always on the lookout for lucrative targets that cost little to infiltrate. Companies can reduce attacks by using encryption, access control systems, and modern security solutions to make network attacks costly for hackers.
Block network attack routes
Common routes for network attacks include open ports, conventional email attachments with viruses, and Trojan horses or drive-by attacks when visiting malware-infected websites. Firewalls and antivirus software are recommended for blocking these routes.
Gone are the days when you could just scan for signatures. Simple pattern matching no longer cuts it in the fight against network attacks.
Prevent security loopholes
Today’s antivirus programs search for similarities to previous intrusions, shut down software suspected of dangerous activity, and allow for the safe encapsulation of malware. Clouds should also be checked on a regular basis.
Automated behavior analysis is a must, for the speed with which new threats arise can no longer be matched by humans on their own resources. But even machine learning tools require human know-how. Nowadays, firewalls may also come with prevention components that search for suspicious patterns.
Leverage technical instruments to root out malware
As systems become more complex and attack vectors become more intelligent, even modern virus scanners and firewalls are no longer sufficient. Plus, negligent workers offer hackers the possibility to bypass security programs and access the company network directly. Special technical instruments are therefore required to root out malware that has made its way into the network undetected.
Use an intrusion detection system
Intrusion detection systems (IDSs) are used to identify suspicious network traffic. These systems may start with switches (for example), where they will skim through data traffic and check for malware. Intrusion prevention systems (IPSs) can also be used to remove malware. The downside of these systems is that they must connect to your system to function. An IPS itself can therefore become an attractive target for hackers. To avoid false alarms during the detection process, the IDS should be incorporated into the company’s security strategy.
While PRTG cannot be used a substitute for an intrusion detection system, it comes with many functions that help to protect against cyberattacks:
In PRTG, “sensors” are the basic monitoring elements. One sensor usually monitors one measured value in your network, for example the traffic of a switch port, the CPU load of a server, or the free space on a disk drive. On average, you need about 5-10 sensors per device or one sensor per switch port.
Paessler conducted trials in over 600 IT departments worldwide to tune its network monitoring software closer to the needs of sysadmins. The result of the survey: over 95% of the participants would recommend PRTG – or already have.
Paessler PRTG is used by companies of all sizes. Sysadmins love PRTG because it makes their job a whole lot easier.
Bandwidth, servers, virtual environments, websites, VoIP services – PRTG keeps an eye on your entire network.
Everyone has different monitoring needs. That’s why we let you try PRTG for free.