Network attacks –
Overview, prevention, monitoring, tips
Systematize your company’s IT security
Stay up to date on “state-of-the-art” technology and new threats
Spread awareness amongst employees
Use modern and intelligent security technologies
Install a network monitoring tool = PRTG
Network attacks
Jump to the topic of your choice
- The threat of network attacks
- Network attacks can do considerable damage
- A systematic approach to IT security
- Preventive measures against network attacks
- Intelligent protection against a variety of network attacks
- Network monitoring as a basis for protection against network attacks
- How PRTG can help
- The PRTG approach to preventing network attacks:
- PRTG for preventing network attacks – scenarios and solutions
- 7 reasons why network monitoring with PRTG increases security
The threat of network attacks
In May of 2017, WannaCry infected more than 230,000 computers in 150 countries with ransomware. The data of the infected computers was encrypted, and money was demanded to restore it. In 2013, three billion Yahoo user accounts were compromised by a cyberattack that took several years to be detected. Companies have never been as vulnerable to network attacks as they are today.
They operate globally, are connected with the entire world, and generate income across the Internet. Companies have come to realize that life in the digital world is not always easy sailing. As their virtual presence grows, so does the number of gateways in their networks. These interfaces are currently being used by hackers in an increasingly professional manner, creating a problem that only gets worse as a company’s IT infrastructure becomes more complex.
Network attacks can do considerable damage
- Sit back, close your eyes, and hope you get lucky? A plan that is not without risks, for a successful attack can do considerable damage:
- Compromised websites and social media accounts (relatively harmless)
- Loss of trust due to leaked customer information or credit card data
- "Ransom" payments to regain access to your systems
- The need to develop new strategies following the theft of business secrets
- Sales losses due to disrupted company activities following DDoS attacks, flooding, or botnets which diminish computing capacity
- Extensive property damage, injuries, or even deaths due to the hacking of critical infrastructures
- Personal liability up to and including the incarceration of management if legal requirements have not been respected
All good reasons to take IT security seriously.
A systematic approach to IT security
With development catapulting during the past few years – from the professionalization of criminal hackers to ever more complex IT infrastructures – IT security is becoming an increasingly important issue when it comes to a company’s business dealings. In order to best meet the dangers posed by network attacks, your security model should take into account the following key objectives:
View IT security as a task that never ends
Technology is in a constant state of development. Software versions have more and more new functions. When one security loophole is closed, another one pops up elsewhere. It seems like whenever new security software is released, there is already a hacker who knows how to crack it. As a result, companies must view IT security as an ongoing process, or a task that never ends.
Create comprehensive security to thwart network attacks
A comprehensive approach is vital. In today’s world, you need much more than just virus scanners and firewalls. IT security has expanded to include updates, training sessions, monitoring, intelligent security tools, and even collaboration with other companies in your sector to address current developments surrounding IT security issues.
Reduce complexity
By simplifying IT structures and keeping the number of tools you use to a minimum, you will already be doing a great deal to ward off potential attacks. All software creates gateways, either by itself or when run with other programs. By keeping things simple, you will close off potential gateways and thus prevent hackers from finding a way inside. A rule of thumb: the more complex your infrastructure, the more vulnerable your system.
Make IT security a key issue
IT security should be a major consideration when starting any new project - and not just for those in charge of security and data protection. IT administrators and software developers must also be up to speed. And while management may pass on specific tasks, it should likewise stay informed of all security developments.
Stick to “state-of-the-art” technology
The law requires that companies use “state-of-the-art” technology, but allows for exceptions in certain situations. Companies must therefore stay up-to-date on all developments with regard to technology. However, because the provisions are quite vague and spread out amongst several different regulations, it is recommended that you seek the advice of a legal professional.
Get employees on the same page
Employee training should also be part of your security model. Your biggest challenge will be to entice employees who have little or no interest in IT security. Because your task is neverending, employee training should become an increasingly proactive part of the model.
Jack up expenses for hackers
Professional hackers have expenses and seek to make profits. They’re always on the lookout for lucrative targets that cost little to infiltrate. Companies can reduce attacks by using encryption, access control systems, and modern security solutions to boost the expenses hackers have to pay to get through.
Preventive measures against network attacks
The best way to prevent network attacks is by reducing the number of weak spots in your network.
Weak spots not only include software flaws, runtime errors, and complex IT infrastructures, but also careless employees.
Addressing software flaws
Nowadays, you have to assume that software is faulty, and that bugs will create gateways. Exploits use weak spots to gain access to external computers and install malware. These exploits are saved in “exploit kits” and sold to interested parties with convenient user interfaces. As a result, weak spots can be “exploited” during attacks with little or no expense at all.
If you discover a weak spot and see that a patch or update is available, you should install the latter as quickly as possible, preferably by way of an automated update distributor that covers all the workstations in your company. By doing so, you’ll minimize the risks posed by software flaws, even if such glitches cannot be eliminated entirely. A company always runs the risk that a hacker will learn of a bug before its software developers.
Addressing human vulnerability
A particularly insidious form of malevolent conduct is social manipulation (“social engineering”). Social engineering is defined as the manipulation of others with the aim of eliciting certain behaviors, such as the disclosure of confidential information or the clicking of a link.
It can take place on a direct level, e.g. as a call by a “service technician” who allegedly needs someone’s login details, or indirectly by coaxing a person to open a certain website or an email which the hacker can then use to access login data or infect a computer. Phishing – especially spear phishing – is extremely dangerous. Phishing targets the masses (with a success rate of around 0.1%), while spear phishing goes after a specific group by sending emails that look authentic.
Intelligent protection against a variety of network attacks
Network attack routes
Other routes for network attacks include open ports, conventional email attachments with viruses, and Trojan horses or drive-by attacks when visiting malware-infected websites. Firewalls and antivirus software are recommended for blocking these routes. Gone are the days when you could just scan for signatures. Simple pattern matching no longer cuts it in the fight against network attacks.
Prevention of security loopholes
Today’s antivirus programs search for similarities to previous intrusions, shut down software suspected of dangerous activity, and allow for the safe encapsulation of malware. Clouds should also be checked on a regular basis. Automated behavior analysis is a must, for the speed with which new threats arise can no longer be matched by humans on their own resources. But even machine learning tools require human know-how. Nowadays, firewalls may also come with prevention components that search for suspicious patterns.
The need for technical instruments
But with systems continually gaining in complexity and attack vectors becoming more and more intelligent, even modern virus scanners and firewalls are no longer sufficient. Above all else, negligent workers offer hackers the possibility to bypass security programs and access the company network directly. Special technical instruments are therefore required to root out malware that has made its way into the network undetected.
Intrusion detection system
Intrusion detection systems (IDSs) are used to identify suspicious network traffic. These systems may start with switches (for example), where they will skim through data traffic and check for malware. Intrusion prevention systems (IPSs) can also be used to remove malware. The downside of these systems is that they must connect to your system to function. An IPS itself can therefore become an attractive target for hackers. To avoid false alarms during the detection process, the IDS should be incorporated into the company’s security strategy.
Network monitoring as a basis for protection against network attacks
A fundamental tool for IT security
Comprehensive network monitoring is vital for maintaining the security of your network, for what good is a firewall that crashes or backup software that malfunctions? With network monitoring software, you can keep a constant eye on firewalls, antivirus software, and backup software, and automatically be warned in the event of trouble.
Network traffic recording
Network traffic recording lets you monitor and check network traffic for unusual behavior. It also helps you determine which data and computers are affected by network attacks that have already taken place. By evaluating data archives, downtime can be reduced substantially, as was even the case for the “WannaCry” ransomware attack.
How PRTG can help
PRTG as an early warning system
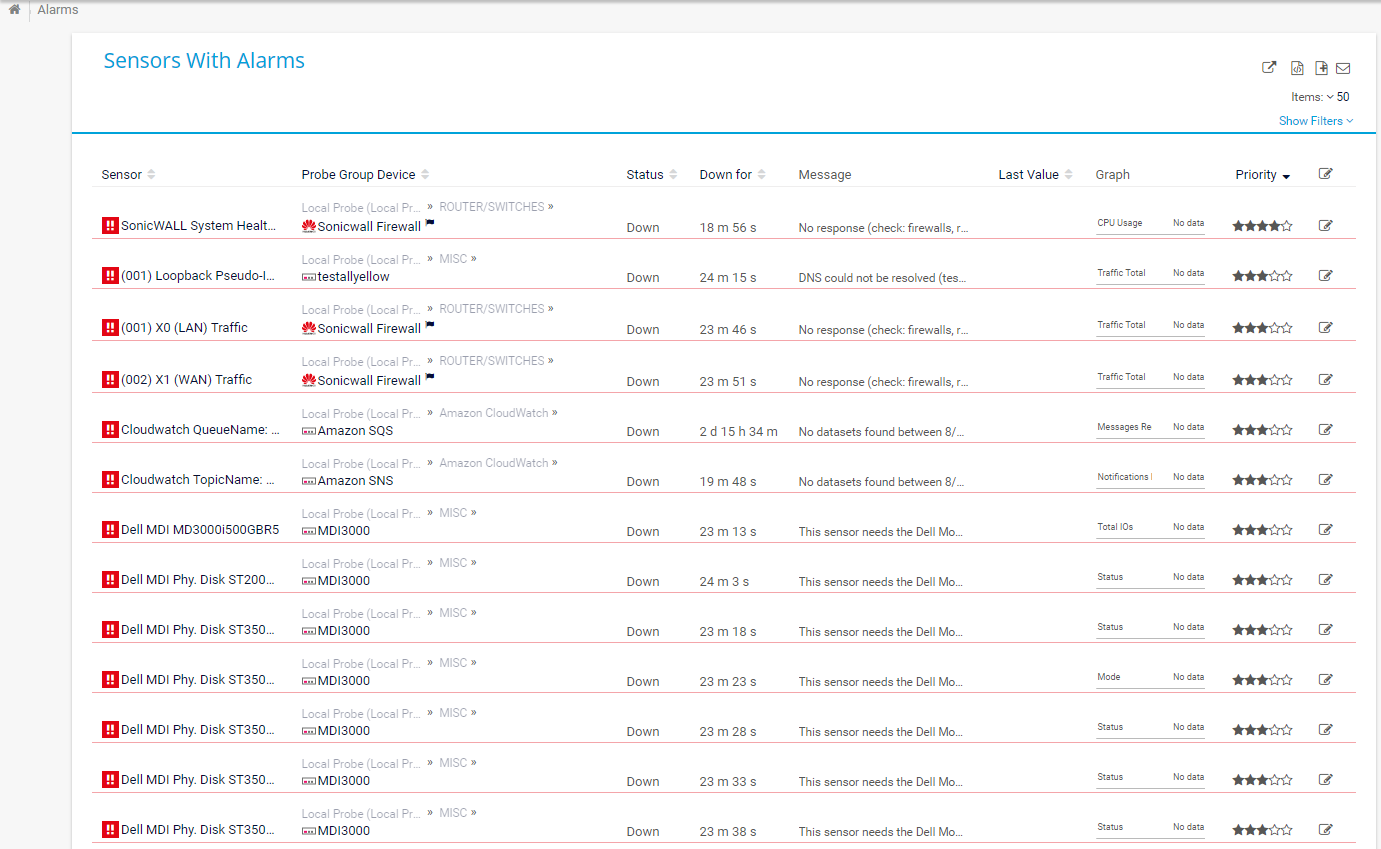
PRTG network monitoring software acts as an early warning system against suspicious activity and anomalies in your network traffic. PRTG seeks to prevent malware which has already infiltrated a network from doing any further damage. While PRTG cannot be used a substitute for an intrusion detection system, it comes with many functions that help to protect against network attacks:
- PRTG monitors your entire network: servers, storage devices, connected devices such as routers, computers, and printers, traffic, etc.
- With our all-in-one monitoring solution PRTG, you can do away with the weak spots which tend to crop up when using a variety of different programs
- Network recording lets you check your data for anomalies
- The recorded data serves as a database for IT security systems
- PRTG checks the functionality of firewalls, virus scanners, security software, and backups, as well as access rights to server rooms and other spaces.
Identify network bottlenecks
To measure network traffic, PRTG uses SNMP, packet sniffing, and NetFlow. SNMP makes it possible to monitor all the traffic in your network, and to sort this traffic by port. Packet sniffing and NetFlow/sFlow/jFlow offer a more detailed analysis of your network traffic. These methods allow you to sort network traffic by IP address or protocol. As a result, you will be able to quickly identify potential network bottlenecks, spot unusual spikes in activity, and shut down applications and computers.
Custom notifications
Network traffic recording makes it easier to determine if a computer is affected by malware. It can help out, for example, when you know what you are looking for but don't exactly know which computer is affected. PRTG warns you in the event of downtime that may be putting the security of your network at risk. Faulty backups are also recorded. Thanks to custom PRTG notifications, you can intervene before further damage occurs.
The PRTG approach to preventing network attacks:
Traffic monitoring
Firewall monitoring
Virus scanner monitoring
PRTG for preventing network attacks – 2 scenarios and solutions
Network recording – what got hit?
- Determine the details of the attack
- Retrieve the network traffic recording history
- Search for specific attack patterns
- Shut down the affected computer and/or applications
Check traffic for anomalies
- Enable traffic monitoring sensors
- Set up notifications and threshold values for traffic parameters
- Search for unusual patterns such as inexplicable load peaks or abnormally heavy traffic
- Introduce countermeasures
Trusted by 500,000 users and recognized
by industry analysts as a leader
“Fantastic network and infrastructure monitoring solution that is easy to deploy and easier still to use. Simply the best available.”
“Software is absolutely perfect, Support is superior. Meets all needs and requirements, this is a must have solution if you are needing any form of monitoring.”
“The tool excels at its primary focus of being a unified infrastructure management and network monitoring service.”
7 reasons why network monitoring with PRTG increases security
How PRTG defines sensors
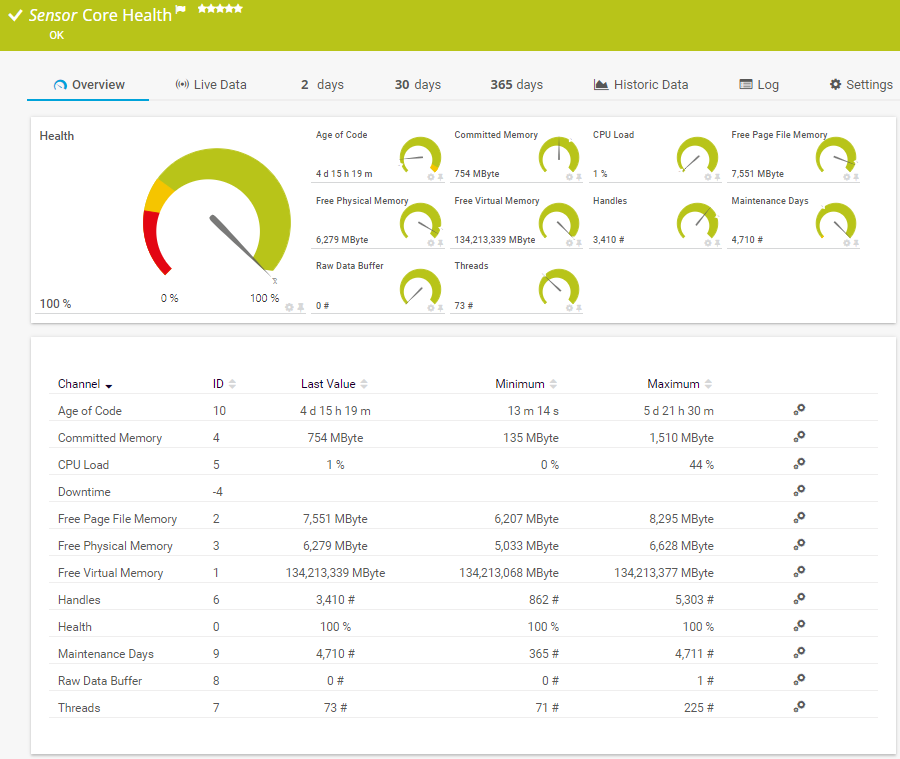
In PRTG, “sensors” are the basic monitoring elements. One sensor usually monitors one measured value in your network, e.g. the traffic of a switch port, the CPU load of a server, the free space of a disk drive. On average you need about 5-10 sensors per device or one sensor per switch port.
Keep an eye on your network data and IT infrastructure
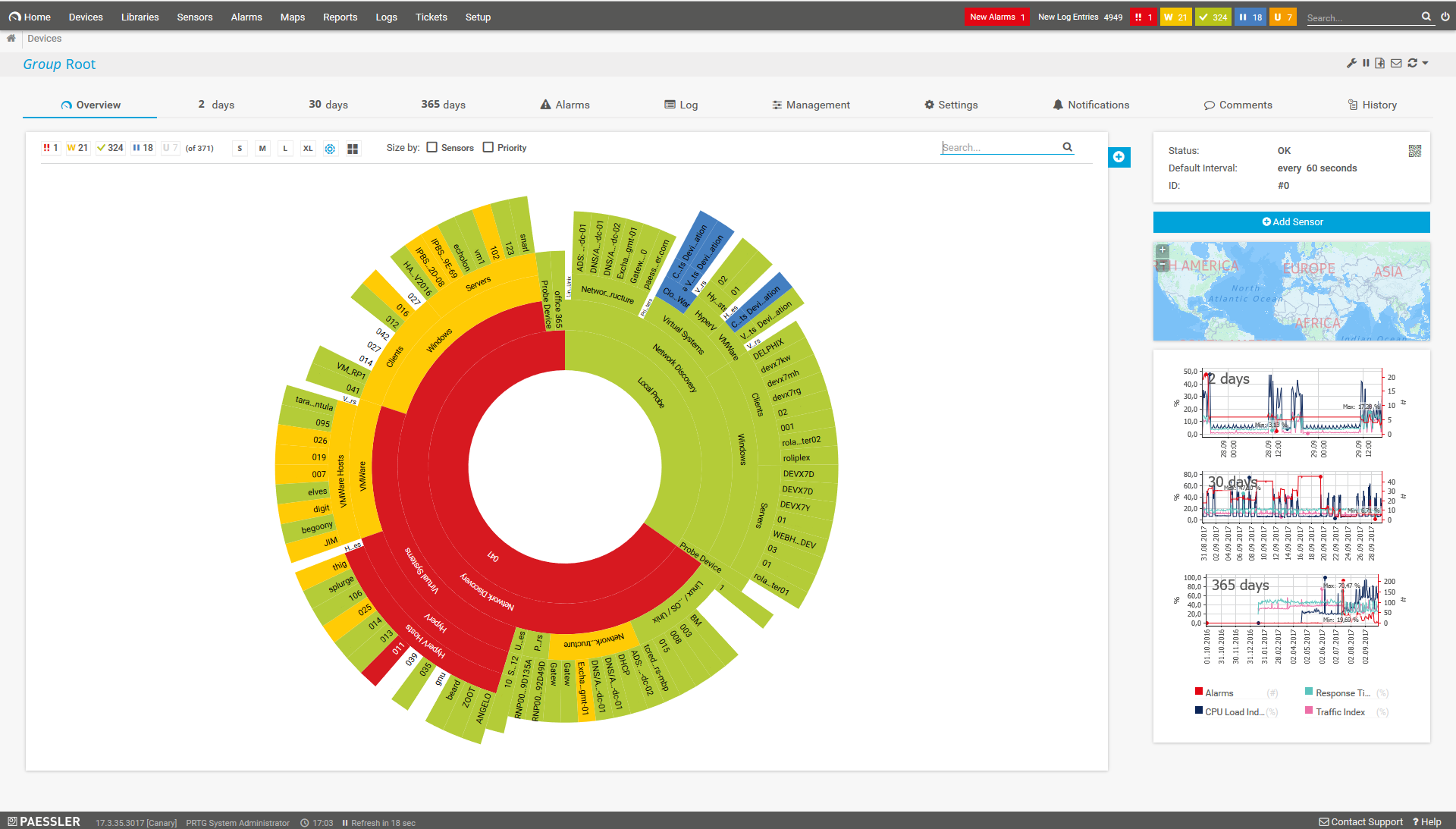
An easy-to-read dashboard provides an overview of your monitoring data. You can also have interrelated data displayed on your dashboard to establish correlations and draw conclusions.
Customize sensors to detect threats
The powerful PRTG API provides monitoring that is tailormade for your network’s infrastructure. Sensors can be added with just a few clicks. Thanks to PRTG alerts, you'll be prepared for potential threats to the company network.
All-in-one software for high-performance monitoring
PRTG effectively monitors all the parameters in your monitoring environment. As a result, problems can be found faster, and prevented in the future proactively. This saves both time and money.
Reduce risks and complexity with centralized monitoring
When it comes to monitoring network traffic, PRTG is more effective at reducing risks and complexity than several individual tools working together. Risks arising from weak spots and compatibility problems between tools therefore become obsolete.
Monitoring as an early warning system in the event of suspicious activity
With PRTG, network traffic anomalies are recorded and traced. Furthermore, hackers who have already infiltrated the network are prevented from causing additional damage.
Identify affected computers more easily
Thanks to the recorded network traffic data, it is easier to identify computers that have been affected by an attack, and to recover these computers one-by-one via countermeasures or the restoring of a backup or image.
Protect your security tools
By monitoring firewalls, antivirus software, and other security tools, PRTG can warn you in the event of downtime that may be posing a security risk to your network. Faulty backups are also recorded. You can therefore take action before things go awry.
PRTG makes your job easier
Our monitoring software frees you to focus on other tasks by promptly notifying you of potential issues.
Save effort
PRTG gives you one central monitoring tool for your servers and entire network. Enjoy a quick overview of your whole infrastructure via our dashboard and app.
Save time
Getting started with PRTG is a breeze. Setting up or switching from another network monitoring tool is easy thanks to the auto-discovery and pre-configured device templates.
Save money
80% of our customers report substantial cost savings with network monitoring. Your costs of licenses will likely pay for themselves within weeks.
“Easy to implement and configure with good technical support.”
R. v. S., ICT Manager at Heinen & Hopman Eng BV

“The greatest advantage of PRTG? You get to rest easy.“
Steffen Ille, Bauhaus-University of Weimar, Germany
Your network security at a glance – even while on the go
Set up PRTG in minutes and use it on almost any mobile device.

PRTG: The multi-tool for sysadmins
Adapt PRTG individually and dynamically to your needs and rely on a strong API:- HTTP API: Access monitoring data and manipulate monitoring objects via HTTP requests
- Custom sensors: Create your own PRTG sensors for customized monitoring
- Custom notifications: Create your own notifications and send action triggers to external systems
- REST Custom sensor: Monitor almost everything that provides data in XML or JSON format
Still not convinced?
More than 500,000 sysadmins love PRTG
Paessler PRTG is used by companies of all sizes. Sysadmins love PRTG because it makes their job a whole lot easier.
Still not convinced?
Monitor your entire IT infrastructure
Bandwidth, servers, virtual environments, websites, VoIP services – PRTG keeps an eye on your entire network.
Try Paessler PRTG for free
Everyone has different monitoring needs. That’s why we let you try PRTG for free. Start now with your trial.
|
PRTG |
Network Monitoring Software - Version 24.2.94.1400 (April 10th, 2024) |
|
Hosting |
Download for Windows and cloud-based version PRTG Hosted Monitor available |
Languages |
English, German, Spanish, French, Portuguese, Dutch, Russian, Japanese, and Simplified Chinese |
Pricing |
Up to 100 sensors for free (Price List) |
Unified Monitoring |
Network devices, bandwidth, servers, applications, virtual environments, remote systems, IoT, and more |
Supported Vendors & Applications |
|





Combining the broad monitoring feature set of PRTG with IP Fabric’s automated network assurance creates a new level of network visibility and reliability.