I want to avoid the web browser security warning that is shown when using the PRTG default SSL certificate and a secure https connection. How can I get, install, and use such a certificate with PRTG?
How can I use a trusted SSL certificate with the PRTG web interface?
Votes:
0
16 Replies
Votes:
1
This article applies as of PRTG 22
General information: Trusted SSL certificates and PRTG
PRTG comes with a default SSL certificate for the PRTG web server. This way, all communication between your browser and PRTG is encrypted via SSL and you can securely use the PRTG web interface via HTTPS.
Certificate warnings
This certificate does not match the DNS name (or IP address) of your PRTG installation, so web browsers always show a warning message The certificate is not correct when you connect to the PRTG web interface.
The role of SSL certificates
SSL certificates play two roles: First, they encrypt data (for example, passwords from your PRTG installation). Their second role is to ensure that you are actually connected to the correct server (to avoid man-in-the-middle attacks, for example). Traffic encryption starts working immediately after you have finished installing PRTG.
Install certificate files
To avoid the browser warnings, install a trusted certificate for the PRTG web server (in PEM-encoded format). The PRTG web server implements OpenSSL and expects certificate files in the same format that is used for Apache web servers, too.
PRTG needs the following files, correctly named, that contain data in the expected encoding and format:
- prtg.crt: The certificate of your server
- root.pem: The root certificate of the certificate issuer
- prtg.key: The private key of your server
This can sometimes make the manual import of an issued certificate a bit tricky. There might be various certificate files that you get from a certificate authority (CA), and the private key is usually encrypted. This is why we provide the freeware tool PRTG Certificate Importer that makes the installation of a trusted certificate for your PRTG core server much easier.
Note: Usually, your certificate provider sends you the key in encrypted format. PRTG Certificate Importer decrypts it automatically with the according password. If you want to import a certificate manually, use the key password in combination with external tools (for example, OpenSSL) to create a decrypted key file. PRTG does not accept an encrypted key file. You can check if the key matches your certificate here.
PRTG Certificate Importer
Use PRTG Certificate Importer to install a trusted certificate for PRTG
PRTG Certificate Importer automatically combines and converts all files issued by a CA for the use with PRTG and saves the certificate files to the correct path on your PRTG core server.
General remarks
| Important notice: We strongly recommend that you make backup copies of the default PRTG certificate files before you replace them. PRTG Certificate Importer does this automatically by default. |
In some cases, your certificate provider gives you certificates and key files in the correct PEM-encoded format already. However, you may receive a single file that contain several elements, for example, several certificates along with a private key that belongs to the certificates. Such a file might be called *.chain.pem or similar.
A certificate begins with -----BEGIN CERTIFICATE----- and ends with -----END CERTIFICATE-----
A key begins with -----BEGIN PRIVATE KEY----- and ends with -----END PRIVATE KEY-----
PRTG Certificate Importer can usually handle such a combined file correctly, which is why we recommend that you use this tool.
Manual certificate import
For a manual certificate import without using PRTG Certificate Importer, you must follow the steps below.
Note: We do not recommend that you manually import certificates. Use PRTG Certificate Importer instead.
- Open the file in a text editor and copy one certificate (if there are several, take the first one) into a new text file and save it as prtg.crt.
- Copy the key into a new text file and save it as prtg.key.
- Identify the root certificate of the issuer, which is most likely the last certificate listed before the key. It looks similar to the server certificate you copied in the step before.
- Copy the root certificate into a new text file and save it as root.pem. Alternatively, you can download the PEM-encoded root certificate from your issuer's website.
- Save the file as root.pem.
- Stop the PRTG core server service, copy the three files into the \cert folder of your PRTG program directory (copy the existing files to a safe location), and restart the PRTG core server service.
What can I do if PRTG does not start after replacing the default certificate?
If something went wrong, copy the three default PRTG certificate files to the \cert folder of your PRTG program directory again. We recommend that you back up the default certificate before changing anything.
Next, open your PRTG Administration Tool on the PRTG core server system and start the PRTG core server again.
If you did not back up the default certificates and they are no longer available, delete the \cert folder and install PRTG over the existing installation.
Different naming for former PRTG versions
Note: For PRTG versions 7, 8, and 9, file names are different from the ones shown above. If you want to use your own SSL certificate files with these former PRTG versions, name them prtg7.crt, root.pem, and prtg7.key.
There are several options to get the required certificate files. See the other answers in this thread for more information.
What should I do if I receive the error "Certificate cannot be used for server authentication"?
Make sure that you have set the attribute extendedKeyUsage = serverAuth. Otherwise, you cannot use this certificate for SSL.
| Important notice: You must adopt your own settings, Subject Alternative Names (SAN), and other attributes when creating your own certificates. Note that we cannot provide support in this case. We recommend that you obtain certificates via one of the methods in this thread. |
In this thread
- Using a free trial SSL certificate (InstantSSL)
- Using a certificate from a Microsoft CA server
- Quick and easy: Using an existing (wildcard) certificate
- Set up your own certification authority
- Certificates for PRTG(Apache) from PFX file
- Using a GoDaddy SSL certificate with PRTG
- Using a DigiCert SSL certificate with PRTG
Note: StartCom is not a CA anymore and stopped issuing new StartSSL certificates on January 1st, 2018, so we removed the description for StartSSL from the article.
More
- PRTG Certificate Importer—Installing Trusted SSL Certificates for PRTG Network Monitor
- For a general overview, see How can I establish a secure web interface connection to PRTG?
- For general questions about SSL, find a good overview in the SSL FAQ at SSLShopper.com
- Free certificate tools, for example an SSL file converter: SSL Certificate Tools at SSLShopper.com
- The Most Common OpenSSL Commands
- For step-by-step instructions, see the other answers to this question.
Created on Feb 2, 2010 3:29:59 PM by
Daniel Zobel [Product Manager]
Last change on Jan 2, 2023 2:49:09 PM by
Brandy Greger [Paessler Support]
Votes:
0
This article applies as of PRTG 22
Using a free trial SSL certificate (InstantSSL)
The encryption of traffic already works after you installed PRTG. To stop the browser warnings, you must install a trusted certificate. This article explains how you can do this with a certificate from Comodo InstantSSL. Apart from fee-based certificates, they also offer free 30-day-certificates that you can use for PRTG.
Step 1: Download the PRTG Certificate Importer
The PRTG Certificate Importer automatically combines and converts all files issued by a certificate authority (CA) for the use with PRTG. It also saves the certificate files to the correct path on your PRTG core server.
Step 2: Install OpenSSL
- Download Win32 OpenSSL here and install it. By default, the OpenSSL files are installed to the folder C:\Program Files (x86)\OpenSSL-Win32\.
- If you see this error upon installation, you must also download and install Visual C++ 2008 Redistributables:
"The Win32 OpenSSL Installation Project setup has detected that the following critical
component is missing: Microsoft Visual C++ 2008 Redistributables. Win32 OpenSSL does
not function properly without this component. We recommend that you install the
missing component before clicking OK to continue."
Download the files here.
Step 3: Create your CSR (Certificate Signing Request)
- Open a command prompt and go to to the C:\Program Files (x86)\OpenSSL-Win32\bin folder where the openssl.exe is located. You can do this by typing cd C:\Program Files (x86)\OpenSSL-Win32\bin.
- Enter the following command:
openssl req -nodes -newkey rsa:2048 -keyout prtg.key -out prtg.csr -config openssl.cfg
- Answer the questions that appear in the command prompt.
- The Common Name question is the most important: Here, you must enter the domain name or IP address that you want to securely use with the PRTG web server. Your screen should look like this:
C:\Program Files (x86)\OpenSSL-Win32\bin>openssl req -nodes -newkey rsa:2048 -keyout prtg.key -out prtg.csr -config openssl.cfg Loading 'screen' into random state - done Generating a RSA private key ..................++++++ .......................................++++++ writing new private key to 'prtg.key' ----- You are about to be asked to enter information that is incorporated into your certificate request. What you are about to enter is what is called a Distinguished Name or a DN. There are several fields, but you can leave some of them blank. For some fields, there is a default value, If you enter '.', the field is left blank. ----- Country Name (2 letter code) [AU]:DE State or Province Name (full name) [Some-State]:Bavaria Locality Name (eg, city) []:Nuremberg Organization Name (eg, company) [Internet Widgits Pty Ltd]:Paessler AG Organizational Unit Name (eg, section) []:IT Common Name (e.g. server FQDN or YOUR name) []:prtg.paessler.com Email Address []:[email protected] Enter the following 'extra' attributes to be sent with your certificate request A challenge password []:. An optional company name []:. C:\Program Files (x86)\OpenSSL-Win32\bin>
- Note: For more information, see the Comodo website. Make sure to follow Comodo's guideline when you generate your CSR:
When generating your CSR, also make sure to enter your details as follows:
Country Name: US
State or Province Name: NJ
Locality Name: Jersey City
Organization Name: Comodo
Common Name: www.domain.com
- There are now two new files in the C:\Program Files (x86)\OpenSSL-Win32\bin folder:
- prtg.key: Contains a private key. Do not disclose this file to anyone.
- prtg.csr: This is your certificate request file that must be sent to the CA.
Step 4: Request your certificate from instantssl.com
- Go to the InstantSSL website and select InstantSSL Trial Certificate. This gives you a free certificate that works for 30 days. Alternatively, you can select one of the other plans.
- Open the prtg.csr file in a text editor. Copy and paste all of the contents to the instantssl website (make sure to copy everything in the file, including -----BEGIN CERTIFICATE REQUEST----- and -----END CERTIFICATE REQUEST-----).
- For Select the server software used to generate the CSR select OTHER and click Agree at the bottom of the page.
- Depending on the type of certificate, Comodo starts a validation process and might send you emails with further instructions.
Step 5: Preparing the certificate files for PRTG
- As soon as the validation process is completed, Comodo provides you with a .zip file that contains one file with the name of your PRTG domain as well as a few other .crt files. In our sample, the files were:
- prtg_paessler_com.crt (the server certificate)
- AddTrustExternalCARoot.crt
- ComodoUTNSGCCA.crt
- EssentialSSLCA_2.crt
- UTNAddTrustSGCCA.crt
- Save the certificate files to one directory, together with the private key that you obtained before.
If you have not done so yet, download the PRTG Certificate Importer to import these files correctly for PRTG. If you do not use the PRTG Certificate Importer, you must do the following:
- Rename the first file (the server certificate file) to prtg.crt.
- Open all other files in a text editor, combine the contents of all files into one file, and save it as root.pem (simply copy them to one file, the order is not relevant).
We do not recommend that you manually import certificates.
Step 6: Copy the files to the /cert folder of your PRTG installation
Use the PRTG Certificate Importer for this step. Open the PRTG Certificate Importer and follow these steps:
- Provide the path to the downloaded certificate files and to the private key.
- Finish if the validation was successful and switch PRTG to a secure HTTPS server in the PRTG Administration Tool section PRTG Web Server.
You can now access your PRTG web interface via HTTPS.
If you want to manually import the InstantSSL certificate:
| We do not recommend that you manually import certificates. Use instead the PRTG Certificate Importer. |
- Copy the following files to the /cert folder of your PRTG Network Monitor installation (make a copy of the existing demo certificates as a backup):
- prtg.crt (the certificate of your server)
- root.pem (the root certificates of the issuer)
- prtg.key (the private key of your server)
- Open the PRTG Administration Tool on the PRTG core server system. On the PRTG Web Server tab, select Secure HTTPS Server.
- Now restart the PRTG Network Monitor core server service and access the website via HTTPS.
- We recommend that you always back up your certificate files.
Created on Feb 2, 2010 4:00:04 PM by
Daniel Zobel [Product Manager]
Last change on Mar 4, 2022 1:19:23 PM by
Brandy Greger [Paessler Support]
Votes:
1
This article applies as of PRTG 22
Using a certificate from a Microsoft CA server
The encryption of traffic already works after you installed PRTG. To stop the browser warnings, you must install a trusted certificate. This article explains how to generate a custom certificate from a Microsoft CA server and how to activate the respective functionality in PRTG.
Install the root certificate
Install your Microsoft CA Root certificate on all machines that are to access the PRTG web interface URL. You can do so via GPO (Group Policy object). For details, see this link:
Create a certificate signing request (CSR)
Use Open SSL to create a CSR. For details, see the article about InstantSSL.
Create a certificate chain
- Go to your Microsoft CA server's web interface via Internet Explorer.
- On the Welcome page, select the task Request a Certificate.
- On the Request a Certificate page, click Advanced Certificate Request.
- You are now on the Submit a Certificate Request or Renewal Request page:
- Open the CSR you generated before, copy the content, and paste it into the Saved Request field.
- In the section Certificate Template, select Web Server.
- Click Submit.
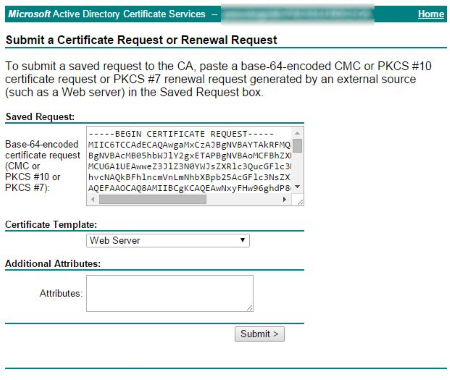
Step 4: Submit your Certificate Signing Request
- On the Certificate Issued page, choose Base 64 Encoded and click Download Certificate Chain.
You can use the resulting certificate chain file (for example, *.p7b) with the PRTG Certificate Importer to install the trusted certificate on your PRTG core server.
Import the certificate
Use the PRTG Certificate Importer to import the certificate for PRTG:
- Download the PRTG Certificate Importer and run it.
- Provide the directory to the certificate chain that you downloaded from the Microsoft CA server.
- Start the import process.
- If the validation was successful, open the PRTG Administration Tool on the PRTG Core Server System and select Secure HTTPS Server on the PRTG Web Server tab.
You can now access the PRTG web interface via HTTPS.
Created on Feb 2, 2010 4:32:32 PM by
Daniel Zobel [Product Manager]
Last change on Mar 4, 2022 1:20:48 PM by
Brandy Greger [Paessler Support]
Votes:
1
This article applies as of PRTG 22
Quick and easy: using an existing (wildcard) certificate
If you already have a certificate that is certified for the (sub-) domain from which you access the PRTG web interface from, you can use it with PRTG.
What you need
- Certificate of your server (for example, xyz.example.com). You can usually download it from the supplier's web page.
- Root certificate of the issuer (if there is more than one, copy all of them into one root certificate .text file. The order does not matter.) You can usually download it from the supplier's web page.
- Private key of your server. You can usually download it from the supplier's web page or the supplier sends it to you.
Import the certificate
Use the PRTG Certificate Importer to install the wildcard certificate on your PRTG core server:
- Download and run the PRTG Certificate Importer.
- Provide the paths to your certificate files.
- After the PRTG Certificate Importer has installed the certificate on your server, open the Setup | System Administration | User Interface and switch to Secure HTTPS server in the PRTG Web Server section.
You can now access the PRTG web interface via HTTPS.
Manual certificate import
Only go through the following steps if you do not use the PRTG Certificate Importer. Note that we do not recommend that you manually import certificates.
Converting and encrypting
Open your certificate files in a text editor. Make sure your certificates and key files are PEM-encoded. Look at the original PRTG certification files to get an idea what PEM-encoded files should look like. If necessary, use an SSL converter tool.
The private key must be decrypted. If the private key is encrypted (this is indicated in the file), use the private key file in combination with the password your issuer has provided you to generate another private key file that is not encrypted:
- Download openssl.
- In the command line, run:
openssl rsa -in [encrypted-key].key -out prtg.key - At the Enter PEM pass phrase prompt, enter the password for the key.
Copy and rename the files
Once you have collected or created the files, copy them to the /cert subfolder of your PRTG program directory. We recommend that you back up the existing files in this folder for later recovery. If necessary, rename your new files as follows:
- prtg.crt (the certificate of your server)
- root.pem (the root certificate of the issuer)
- prtg.key (private key of your server, decrypted)
Final settings for PRTG
- Open the PRTG Administration Tool on the Core Server System and select Secure HTTPS Server on the Web Server tab.
- Restart the PRTG core server service. You can now access the PRTG web interface via HTTPS.
Created on Feb 3, 2010 12:57:08 PM by
Daniel Zobel [Product Manager]
Last change on Mar 4, 2022 1:22:21 PM by
Brandy Greger [Paessler Support]
Votes:
0
Set up your own certification authority
If you access your PRTG server from within your own domain only, you can consider setting up your own Certification Authority (CA).
Created on Mar 11, 2010 2:11:20 PM by
Daniel Zobel [Product Manager]
Last change on Dec 4, 2020 3:40:13 PM by
Brandy Greger [Paessler Support]
Votes:
0
In Regards to Option 3: Using a Certificate from a Microsoft CA Server
You must name the files prtg.crt and prtg.key or PRTG service will not start, it seem this was written down for all the other options apart from this one.
Created on Apr 16, 2010 9:40:23 AM
Last change on May 21, 2012 1:54:02 PM by
Daniel Zobel [Product Manager]
Votes:
0
This article applies as of PRTG 22
Certificates for PRTG (Apache) from .pfx file
Use the PRTG Certificate Importer to install certificates from .pfx files on your PRTG core server.
- Download and run the PRTG Certificate Importer.
- Provide the path to your certificate files. You need the .pfx file (cert.pfx) and the intermediate (certification authority) CA bundle for Apache server (renamed to root.pem, for example).
- After the PRTG Certificate Importer has installed the certificate on your server, open the Setup | System Administration | User Interface and switch to Secure HTTPS server in the PRTG Web Server section.
You can now access the PRTG web interface via HTTPS.
Note: An intermediate certificate is a subordinate certificate specifically issued by a trusted root to issue end-entity certificates. The result is a certificate chain that begins at the trusted root CA, continues via the intermediate CA (or CAs), and ends with the SSL certificate issued to you. Such certificates are called chained root certificates. The root and intermediate CA certificates are contained in the ca-bundle file.
Manual certificate import from a .pfx file:
| Note: We do not recommend that you manually import certificates. Use the PRTG Certificate Importer. |
- Download Openssl software.
- Copy the .pfx file (cert.pfx) to your OpenSSL/Bin directory.
- Open OpenSSL in the command line.
- Type in the following command to transform your .pfx file into a .pem file:
openssl pkcs12 -nodes -in cert.pfx -out keys.pem - Go to your OpenSSL/Bin directory and locate the keys.pem file. Open it in a text editor.
- Locate the private key, which includes and is defined by the text -----BEGIN RSA PRIVATE KEY----- .... certificate contents .... -----END RSA PRIVATE KEY----- and copy it.
- Open a new text editor, paste the private key into the text editor, and save as prtg.key.
- Locate the SSL certificate, which includes -----BEGIN CERTIFICATE----- .... certificate contents .... -----END CERTIFICATE----- and copy the SSL certificate.
- Paste the SSL certificate to a new .text file and save it as prtg.crt.
- Download the intermediate CA bundle for Apache server. Save it as root.pem.
- Copy these three files to the \cert subfolder in the PRTG program directory.
- Restart the PRTG core server service.
Note: An intermediate certificate is a subordinate certificate specifically issued by a trusted root to issue end-entity certificates. The result is a certificate chain that begins at the trusted root CA, continues via the intermediate CA (or CAs) and ends with the SSL certificate issued to you. Such certificates are called chained root certificates. The root and Intermediate CA certificates are contained within the ca-bundle file.
Created on Jul 6, 2011 1:51:47 PM by
Patrick Hutter [Paessler Support]
(7,225)
●3
●3
Last change on Mar 4, 2022 1:23:43 PM by
Brandy Greger [Paessler Support]
Votes:
0
This article applies as of PRTG 22
Using a GoDaddy SSL certificate with PRTG
Find detailed information in the following article:
Created on Oct 1, 2013 9:45:18 AM by
Daniel Zobel [Product Manager]
Last change on Mar 4, 2022 1:23:59 PM by
Brandy Greger [Paessler Support]
Votes:
0
This article applies to PRTG Network Monitor 19 or later
Using a DigiCert SSL certificate with PRTG
Find detailed information in the following article:
Created on Oct 28, 2013 4:23:38 PM by
Gerald Schoch [Paessler Support]
Last change on Feb 25, 2022 1:10:00 PM by
Frank Hadasch [Paessler Support]
(0)
●1
Votes:
0
How different is the procedure in Option 3 in a clustered PRTG environment?
Votes:
0
Both the master and failover use the same core and server software so you should be able to replace the certs on the failover the same way as the master and that should work.
Votes:
0
If I access the PRTG server from my enterprise LAN and also from a public IP. Do I need to create 2 different certificates, one for the local IP and other for the public IP?
Votes:
0
@jf_hernandevz: No you don't need separate certificates here, the same certificate is used for the whole web interface. The IP does not matter here.
Votes:
1
Just to update this a little bit, browsers now require SSL certs to have Subject Alternative Names (SAN), that means your request (CSR) needs this info.
I am no expert on this, but just just a few issues getting a internal cert issued by my windows certificate authority (Windows CA).
Step 1, My CA was still windows 2008 (dont ask!), and only handing out sha1 (broswers see this as invalid), I installed a Windows 2016 CA, that defaulted to sha256
Step2, Download and install openSSL to generate a CSR, and do some other things.
Step3, make a config file for openssl
san.cfg
[ req ]
default_bits = 2048
distinguished_name = req_distinguished_name
req_extensions = req_ext
[ req_distinguished_name ]
countryName = countryName
stateOrProvinceName = countryName
localityName = localityName
organizationName = organizationName
commonName = FQDN
[ req_ext ]
subjectAltName = @alt_names
[alt_names]
DNS.1 = servername.domain.LOCAL
DNS.2 = servername
Change "servername" on the last 2 lines
Step 4, run some openSSL commands
:::creates a CSR. creates a private key openssl req -out sslcert.csr -newkey rsa:2048 -nodes -keyout private.key -config san.cfg :::this will prompt you for your windows CA, and output a cert (in the wrong format) certreq -submit -binary -attrib "CertificateTemplate:WebServer" sslcert.csr blah.cer :::this will convert the cer to a pem (the correct format) openssl x509 -inform der -in blah.cer -out blah.pem
open blah.cer and blah.pem in notepad, and copy these to the PRTG Certificate Importer.
Votes:
3
My sincere apologies and all due respect with Dirk and the creators of PRTG. One needs a Doctorate degree to understand how to install a secure certificate in PRTG when most modern systems makes it as simple as running 'certbot'. So I guess asking for simple instructions on how to install Let's Encrypt is out of the question and this item will be deleted by moderation?
Votes:
0
Hello Alain,
We already have a the certificate importer which you can use to import the certificate into the PRTG. If you have a appropriate certificate and private key, it's exactly the 3 step process to deploy it.
- Run the Certificate importer
- Browse the certificate
- Provide the Private key
Refer to the following link: https://www.paessler.com/tools/certificateimporter
Add comment