I have several devices I want to access via SSH using the SSH sensors of PRTG. In the device settings, section Credentials for Linux/Solaris/macOS (SSH/WBEM) Systems, I want to paste a Private Key. Which format do I need and how does this all work?
How can I use private keys for my SSH sensors with PRTG?
Votes:
0
3 Replies
Votes:
0
This article applies as of PRTG 22.x.76
How to use a private key with SSH sensors in PRTG
SSH sensors in PRTG require credentials for Linux/Solaris/macOS (SSH/WBEM) systems. You can either use a password or a private key to authenticate against the corresponding system. If you want to use a private key, make sure that you meet the following requirements:
- Provide the key in OpenSSH PEM format.
- The key may not be encrypted. PRTG does not support password-protected keys.
- The key must be an RSA, ECDSA, or ED25519 key. PRTG does not support DSA keys.
- When you provide an unencrypted RSA private key in OpenSSH PEM format, copy the entire key, including the lines
-----BEGIN RSA PRIVATE KEY-----and-----END RSA PRIVATE KEY-----or-----BEGIN OPENSSH PRIVATE KEY-----and-----END OPENSSH PRIVATE KEY-----
For more information, see PRTG Manual: Monitoring via SSH.
In this article, we show you how to convert your existing PuTTY RSA key with PuTTYGen to use it with PRTG.
Preconditions:
- An already generated private key.
Note: If you want to use a newly created RSA private key, use the following Linux command and use the created key directly:ssh-keygen -t rsa -b 4096 - A corresponding public key that already exists on the target system. The key is usually stored in the user’s /.ssh/authorized_keys file.
Note: You can also use PuTTYgen to generate a private/public key pair for your systems. For more information, see Generating an SSH key pair using PuTTY.
Step 1: Prepare your existing PuTTY private key
- Save your existing PuTTY private key in a text file named mykey.ppk.
Step 2: Download and install PuTTYgen
- Go to the PuTTY Download Page.
- Download and install the correct installer or binary files.
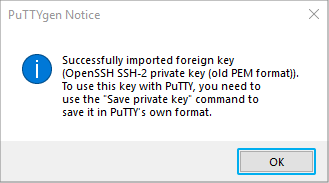
Step 3: Load your key file in PuTTYgen
- Open the PuTTY Key Generator.
- Click Load.
- Navigate to the directory where you have saved the mykey.ppk file in Step 1.
- Load your mykey.ppk file.
You will see the following success message:
Step 4: Export as OpenSSH key file
- To export your key file as OpenSSH key, make sure that you leave the Key passphrase fields empty (1), click Conversions (2) and select Export OpenSSH key (3).
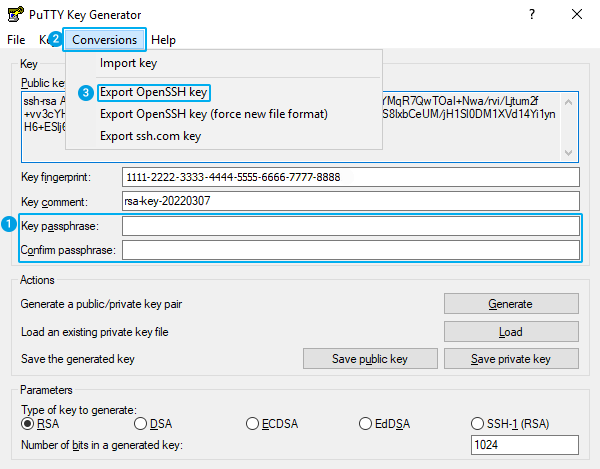
Click to enlarge.
- Confirm the warning message by clicking Yes.
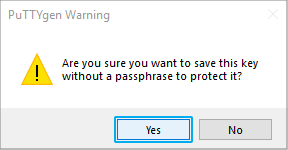
Click to enlarge. - Save the key to a file named mykey-openssh.txt.
- Open this file in a text editor and make sure that there is no line such as:
Proc-Type: 4,ENCRYPTED
| Important notice: If there is a line like the one above, the key is in encrypted format and does not work with PRTG. |
A correct key looks like this, for example:
-----BEGIN RSA PRIVATE KEY-----
MIICWQIBAAKBgGtej3xoYJUrmRvH2/2cQhbIrdwC4+6owbXZCbIoaCSgNf+tl5eZ
848pDe/EcbADdOA+a7E5El3+8k0grjZiFwpjJFgGZgYvdvRyl1rdvYu7l27Qa9OU
[…]
glYyWqk94+bYvo0CQDx8uMBf2Wlc5iKIIlrrEF34eaOg5KWgdb2+SNwl50QxFwW1
r8CUeSuYOykI2PiNU0brMAMgWe68t4HHWWe7ngA=
-----END RSA PRIVATE KEY-----
Step 5: Enter your OpenSSH key in PRTG
- Open the mykey-openssh.txt file that you have created in Step 4 and copy it including the
-----BEGIN RSA PRIVATE KEY-----and-----END RSA PRIVATE KEY-----or-----BEGIN OPENSSH PRIVATE KEY-----and-----END OPENSSH PRIVATE KEY-----lines. - Open the settings of the parent object of the sensors in the PRTG web interface. Navigate to section Credentials for Linux/Solaris/macOS (SSH/WBEM) Systems and set Private key as Authentication Method.
- Paste the entire key, including the BEGIN and END lines in the Private Key field.
- Click Save to your settings.
Note: Once pasted and saved, the private key is shown as:
***************************
| Important notice: If you replace an existing key, you must restart the PRTG core server service for the private key change to take effect. You can restart services in the PRTG web interface under Setup | System Administration | Administrative Tools. |
You can add SSH sensors and use them to query monitoring data.
More
Created on Mar 1, 2012 12:50:56 PM by
Daniel Zobel [Product Manager]
Last change on Jun 19, 2023 4:38:04 PM by
Fruzsina Ébelle [Paessler Support]
Votes:
0
Is it possible to use this Sensor with Password AND Keyfile?
Votes:
0
Hello Michel,
No, either keyfile or password. Both is not possible.
Best,
Sebastian
Add comment